BlackStone Project – More than a pentesting reporting tool. (Update V2.0)

Note: Personally, it is a tool that solves many problems when it comes to creating reports or making use of special features, it is a modular tool, it is in an early phase and it has a lot of potential.
Real hackers help and contribute to the community, as well as share knowledge, just like Micro Joan does.
BlackStone Project 2.0 (For Kali Linux)
BlackStone project or “BlackStone Project” is a tool created by MicroJoan in order to automate the work of drafting and submitting a report on audits of ethical hacking or pentesting.
In this tool we can register in the database the vulnerabilities that we find in the audit, classifying them by internal, external audit or wifi, in addition, we can put your description and recommendation, as well as the level of severity and effort for its correction. This information will then help us generate in the report a criticality table as a global summary of the vulnerabilities found.
We can also register a company and, just by adding its web page, the tool will be able to find subdomains, telephone numbers, social networks, employee emails…
Github: https://github.com/micro-joan/BlackStone
Contents
Install BlackStone
Step 1
cd /opt
git clone https://github.com/micro-joan/BlackStone
cd BlackStone
chmod +x installer.sh
./installer.sh
The application will start automatically but if you log in you will get the 500 error so you must reboot the system and run the installer a second time (this is normal)
Step 2
(reboot system)
cd /opt/blackstone
./installer.sh
USE
Once the installation is complete you can use blackstone from the terminal (with root):
blackstone
Or you can also look for the icon in the system:
LOGIN
User: blackstone
Password: blackstone
Latest news
- Own and automated installer for deployment of BlackStone in Kali Linux.
- Replace Hunter.io results with similar results native to the app.
- Fixed numerous fields sensitive to stored XSS.
- Limitation of access to the BlackStone app only to the computer that runs it (no one on your network that detects your port 80 raised will be able to access this app).
- Insert logo image for each of the clients, instead of automatic logo by favicon (good results were not achieved).
- Automatic subdomain search in the client file, this functionality is native to the BlackStone code itself).
- Fixed various Spanish/English translations.
- System icon integration for BlackStone, the app is added in Kali as a native app with its own launcher.
Use
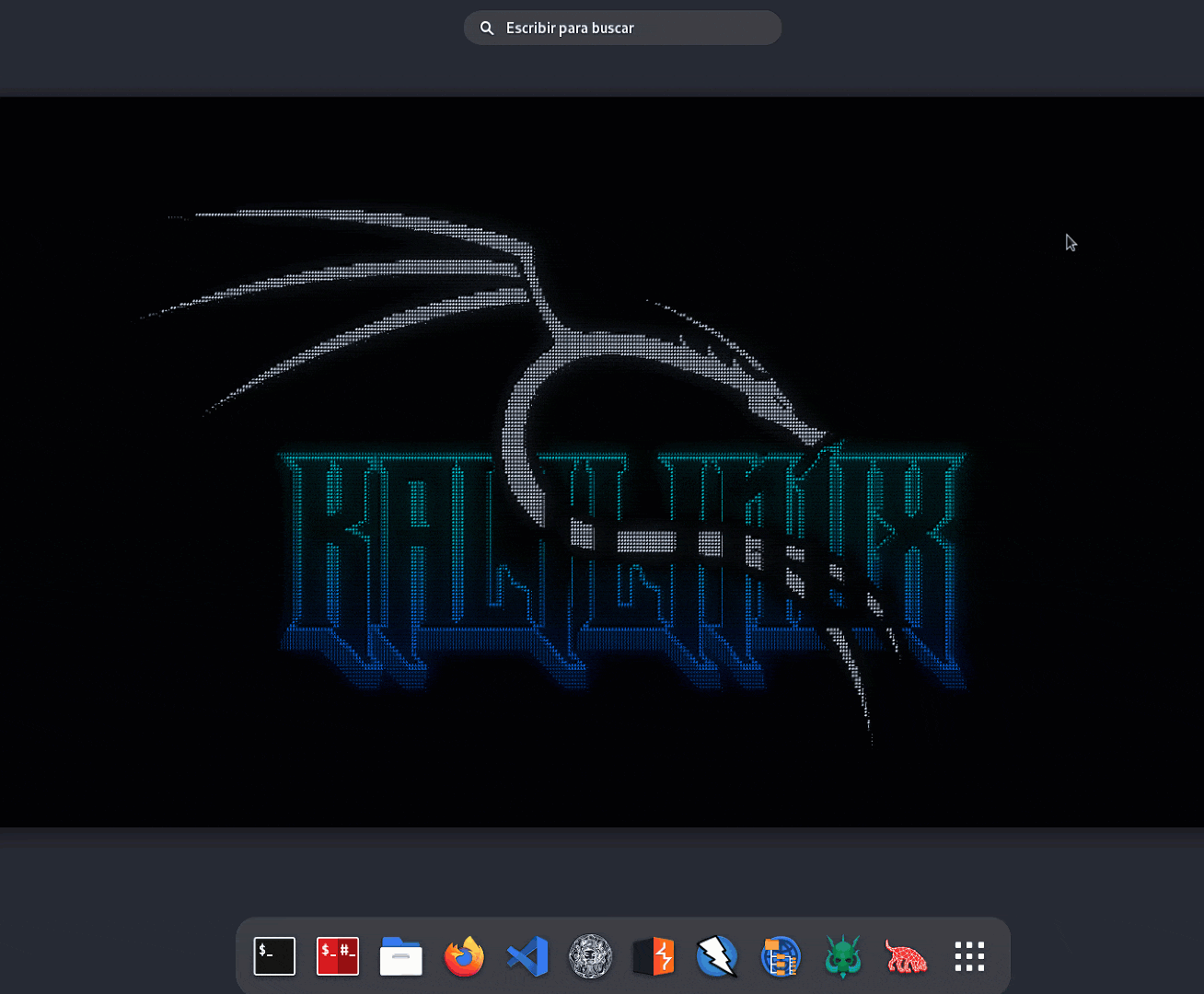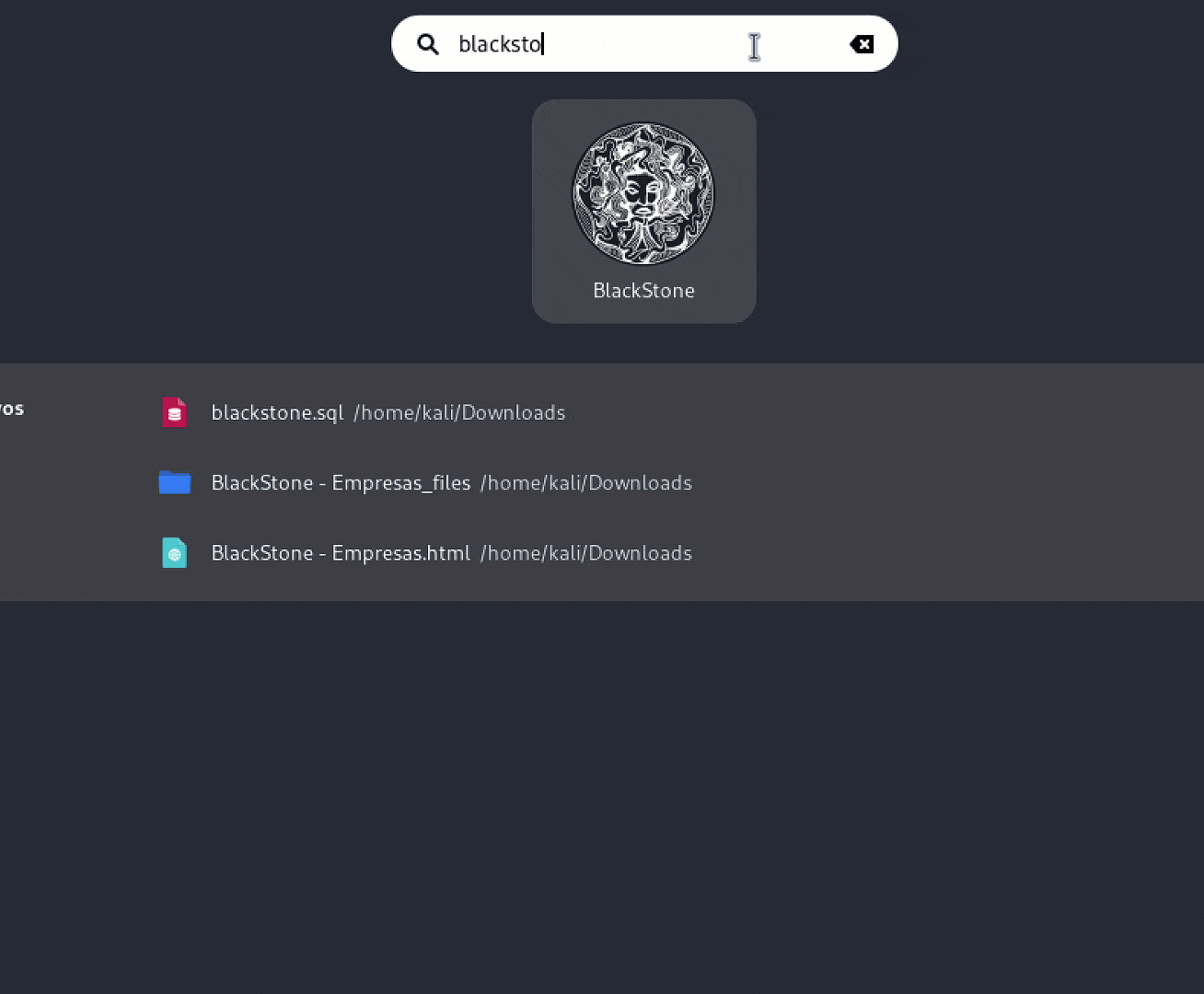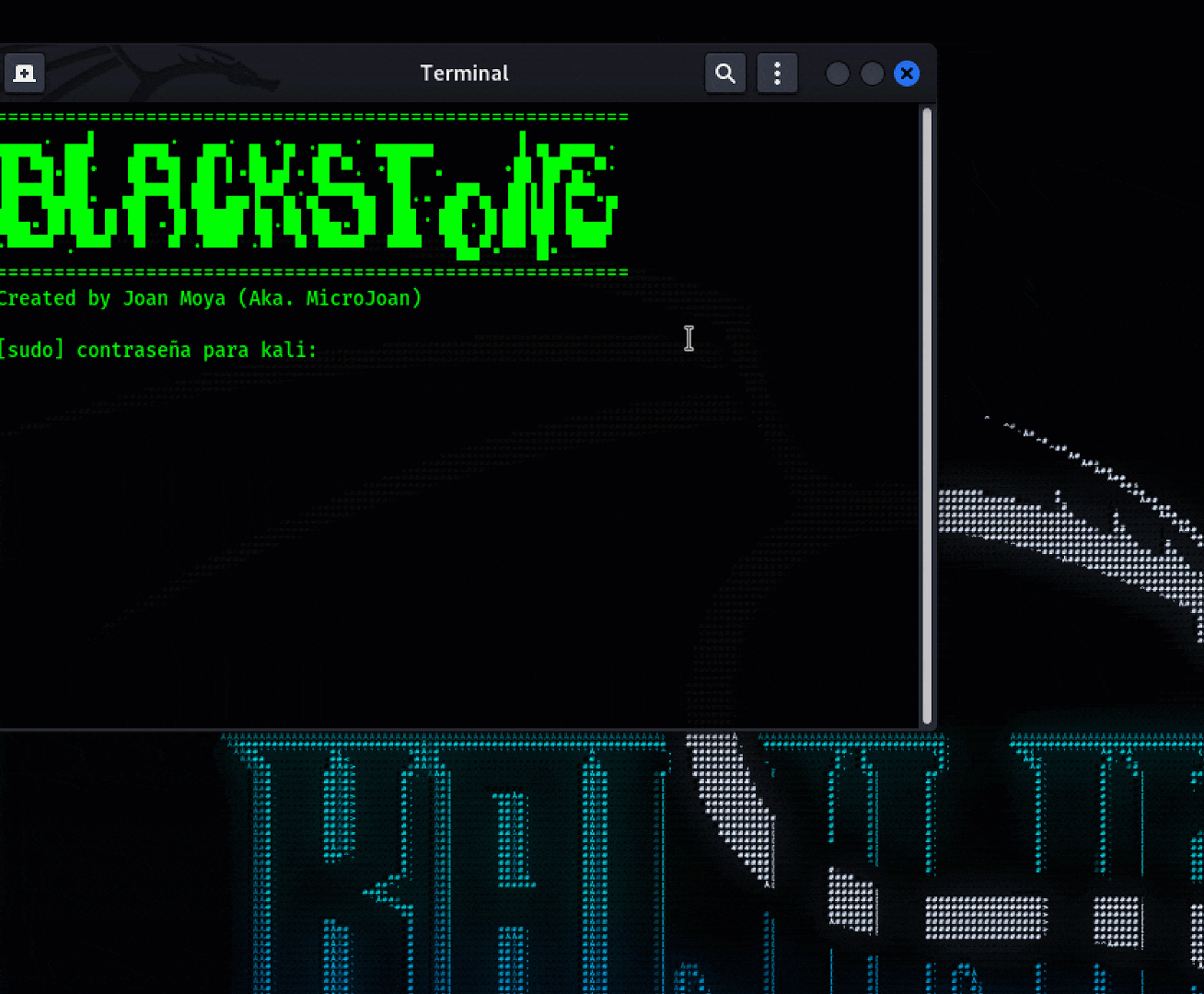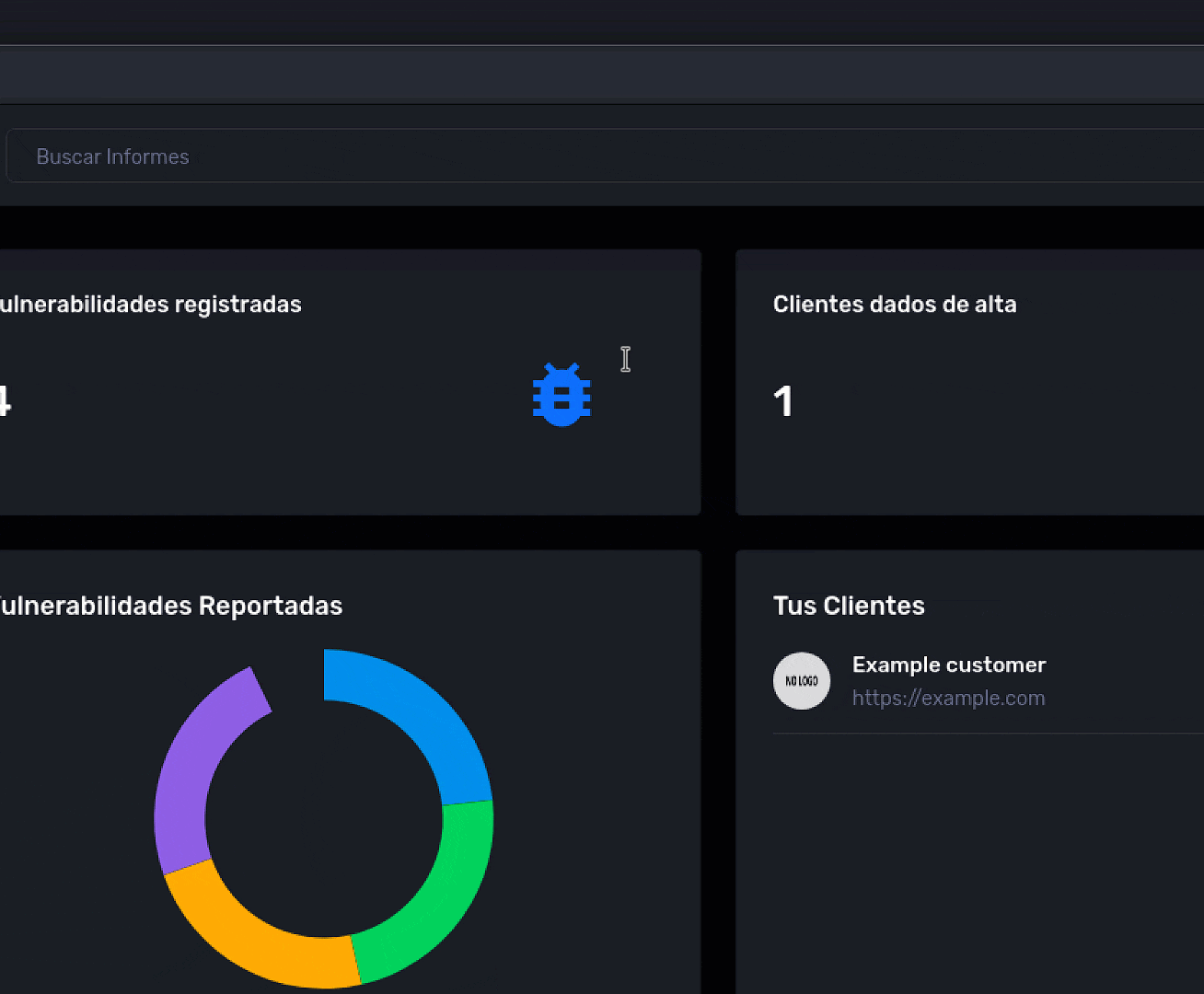
After having vulnerabilities in the database, we will go to the audited client and we will register a client along with their web page, once registered we can go to customer details and we can see the following information:
THE USE OF THIS APPLICATION IS FOR PROFESSIONAL USE, THE AUTHOR IS NOT RESPONSIBLE FOR A MISUSE EMPLOYED
- Subdomains of the website as well as information of interest found in google
- Emails of company workers or SMTP servers

Once we have the company that we are going to audit registered in the database, we will create a report, adding the date, name of the report and the company to which will be audited. When we register the report, we will give it edit and then we will select the vulnerabilities that we want to appear in the report:

Finally, we will generate the report by clicking on the “overview report” button, and later we will save the page that is generated as “.mht”, then we will open it with Word to be able to work on the generated report:

Credits
Original repo: https://github.com/micro-joan/BlackStone
Creator website: https://microjoan.com
Use and installation video: https://youtu.be/qasPlaaYxiU and Subscribe.
Buy him a coffee: https://www.buymeacoffee.com/microjoan


